
Security & Privacy
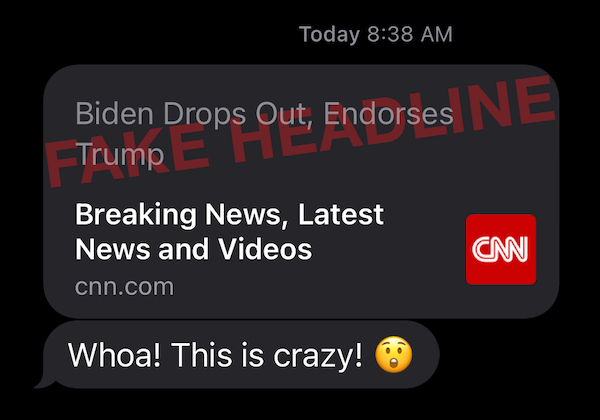
For nearly two years, Apple has neglected to fix a bug that enables anyone to create fake news headlines that appear to come from credible sources.
Although we covered the flaw nearly two years ago, it’s worth questioning why Apple still has not fixed it. This is especially concerning given that we’re in the final days leading up to the 2020 U.S. presidential election.
Other “Big Tech” companies (in particular Twitter, Facebook, and Google) have recently been accused of engaging in or enabling election interference. Perhaps Apple’s neglect should be examined in this context as well.
How does the exploit work?
Originally discovered in February 2019 by the editorial team at MacRumors, there exists an implementation flaw in a Safari browser feature related to link sharing.
The mobile version of Safari (for iPhone, iPad, and iPod touch) allows users to select text from within a Web page before tapping on the Share button, as a means of highlighting a particular portion of a page for the recipient of an iMessage. The feature is intended to allow users to include a quote from an article in the iMessage link preview.
However, Apple does not limit the preview text selection to the contents of the page as received from the Web server, and therein lies the flaw. Users can type something into a page’s search bar (or any other text field), select the text they just typed, tap the browser’s Share button, and then tap the green-and-white Messages icon to send it to an iMessage recipient of their choice.
https://www.intego.com/mac-security-blog/wp-content/uploads/2019/02/iOS-Safari-iMessage-bug-false-headline-demonstration.mp4
The bug as it appeared in iOS 13. It still works the same in iOS 14.1.
Nothing prevents a user from typing a misleading headline or other deceptive text into a field and making it part of the page preview.
It’s worth mentioning that the Messages app on macOS desktop and laptop computers (e.g. iMac, MacBook, etc.) will also display misleading previews sent from Safari on an iOS or iPadOS device.
Why hasn’t Apple done anything to stop this?
When MacRumors editors originally discovered this, they called the flaw “fun” and noted that it could easily be exploited for harmless pranks. However, as we pointed out in February 2019, we feel that all iMessage users should take caution, as the flaw could also potentially be used in more sinister attacks.
We warned last year that this could be exploited as a means to try to get financial investors to buy or sell stocks in a panic based on false headlines, for example.
 Now, in the context of a contentious presidential election, it’s disturbing to see that Apple still has not fixed this flaw. Apple has not even announced plans to mitigate the issue.
Now, in the context of a contentious presidential election, it’s disturbing to see that Apple still has not fixed this flaw. Apple has not even announced plans to mitigate the issue.
The flaw has evidently been present in iOS for years; today we tested devices running the final version of iOS 12 (12.4.8), the current version of iOS (14.1), and even the most recent beta version of iOS (14.2 beta 4). All of these versions of iOS—and corresponding versions of iPadOS—can be used to spread fake news headlines.
Since it seems like this would be an easy thing for Apple to fix (by simply disallowing user input to be part of a link preview), it’s difficult to imagine why Apple has ignored the flaw for nearly two years.
We invited Apple to comment on this story, but company representatives had not responded by publication time. If Apple provides a statement, we will update this article.
Most major news sites are affected
The majority of news sites we tested were vulnerable to this attack.
Following are screenshots showing, as a demonstration, example fake headlines that could be sent from the ABC News, CNN, Fox News, Los Angeles Times, MSNBC, and New York Times homepages.
Although most of these example headlines are a bit silly and unrealistic, one can imagine much more subtle and deceptive headlines that could influence people into changing how they might vote on election day.
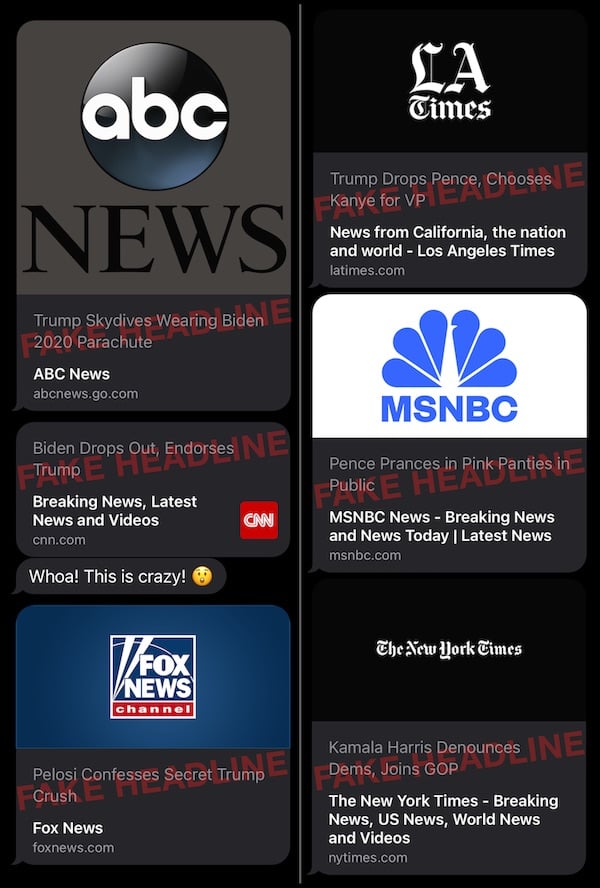
Exploit demo; not seen in the wild. Watermarked to prevent abuse.
A few sites we tested, such as the the main homepages of CBS News and Forbes, seem to be resistant to the bug. More research needs to be done to determine why some sites are resistant while most are not.
Has the attack been used against the 2020 election?
It is impossible to know with any degree of certainty whether this bug has been exploited to spread misinformation to Apple users about this (or any other) election.
Although we have not yet been made aware of any real-world abuse of this exploit, we do know that this bug has been widely known for 20 months, and Apple has chosen not to do anything about it. Apple’s neglect has left ample opportunity for domestic or foreign threat actors to engage in targeted campaigns to deceive individuals in specific communities or demographics, including in swing states.
If you hear of any abuse of this bug for any unethical purposes, whether election interference or stock manipulation or otherwise, please report it to the FBI’s Internet Crime Complaint Center (IC3), and consider leaving a detailed comment on this article. You can also contact the author of this article via Twitter direct message.
How can I learn more?
You can find our original coverage of this Safari bug, from February 2019, here:
iOS Safari flaw allows deceptive news headlines in Messages
Subscribe to our e-mail newsletter and keep an eye here on The Mac Security Blog for updates to this story and all the latest Apple security news.
 You can also subscribe to the Intego Mac Podcast in Apple Podcasts, Amazon Music or Audible, or wherever else you listen to make sure you never miss the latest episode. We discussed this Safari bug way back in episode 71:
You can also subscribe to the Intego Mac Podcast in Apple Podcasts, Amazon Music or Audible, or wherever else you listen to make sure you never miss the latest episode. We discussed this Safari bug way back in episode 71:
Follow Intego on your favorite social and media channels: Facebook, Instagram, Twitter, and YouTube (click the 🔔 to get notified about new videos).

About Joshua Long
Joshua Long (@theJoshMeister), Intego’s Chief Security Analyst, is a renowned security researcher and writer. Josh has a master’s degree in IT concentrating in Internet Security and has taken doctorate-level coursework in Information Security. Apple has publicly acknowledged Josh for discovering an Apple ID authentication vulnerability. Josh’s security research has been featured by many fine publications such as CNET, CBS News, ZDNet UK, Lifehacker, CIO, Macworld, The Register, and MacTech Magazine. Look for more of Josh’s articles at security.thejoshmeister.com and follow him on Twitter.
View all posts by Joshua Long →
Read More
The post Apple neglects to fix “fake headlines” bug usable for election interference appeared first on Malware Devil.
https://malwaredevil.com/2020/10/30/apple-neglects-to-fix-fake-headlines-bug-usable-for-election-interference/?utm_source=rss&utm_medium=rss&utm_campaign=apple-neglects-to-fix-fake-headlines-bug-usable-for-election-interference







 Now, in the context of a contentious presidential election, it’s disturbing to see that Apple still has not fixed this flaw. Apple has not even announced plans to mitigate the issue.
Now, in the context of a contentious presidential election, it’s disturbing to see that Apple still has not fixed this flaw. Apple has not even announced plans to mitigate the issue.





