
First, we’ve updated the look and feel of the entire platform with a new font, icons, and styles. These new styles are not only pleasing to the eye but are designed to be consistent with other CyberArk products and make it easier and more efficient to navigate the Idaptive solution. For example, the headers of each section are now easier to read, new fonts draw the eye to the data that matters most, and new button styles and colors intuitively highlight the next step a user should take to advance their workflow.
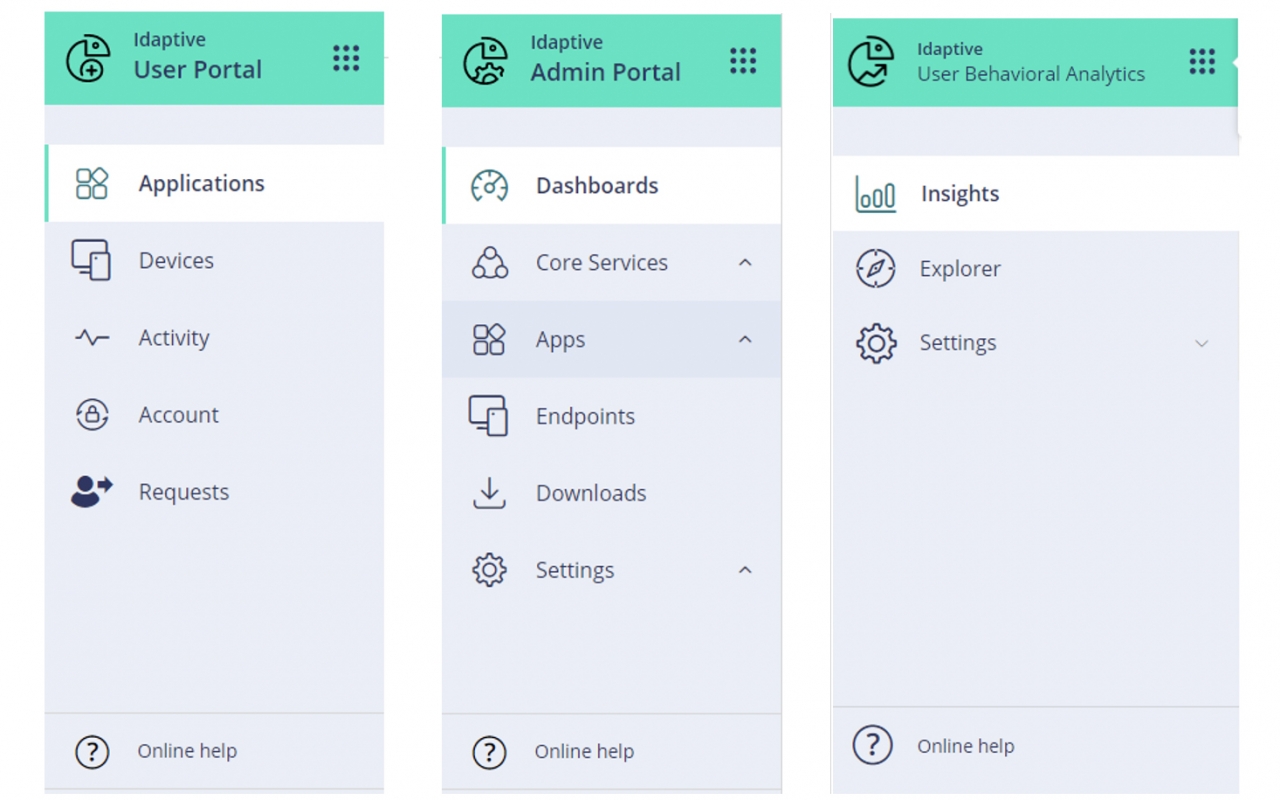
New Navigation Menu
Next, we’ve streamlined the Admin and User Portal navigation menus by standardizing the navigation location, adding the portal switcher toggle icon at the top, and the online help shortcut at the bottom of the menu. In the classic UI, some of these functions were not placed in consistent locations or were hidden in sub-menus. For example, the User Portal navigation menu was at the top of the screen while the Admin Portal menu was on the left. In addition, the option to toggle between Admin, User, and Analytics portals was hidden in one of the drop-down menus. We found through user research that most of the users with admin privileges preferred to standardize the navigation menu location across all portals, and some found the location of help options and portal switch toggle confusing. So we placed them prominently on the left side of the screen. This is one example of a principle you’ll see applied throughout the new UI – simplifying the experience and navigation for every user.
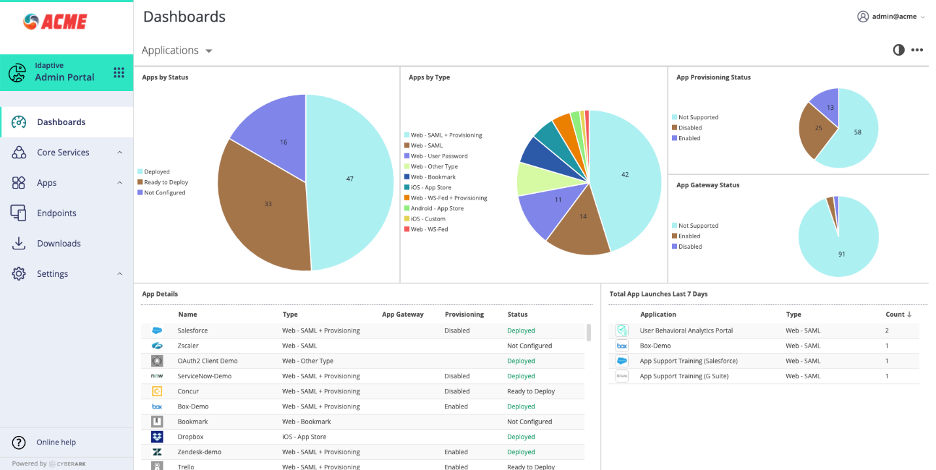
All of these enhancements will be available in the 20.4 Idaptive product release, scheduled for the end of September. Existing customers, as well as new customers, will land in the new user interface by default upon logging in after the product update. We’ll continue to make additional UI enhancements to the Idaptive product in the upcoming releases.
As always, we’re eager to hear what you think. If you have feedback on these enhancements or ideas for additional enhancements you’d like to see, please submit them on our Tech Community page.
Thank you,
The CyberArk Idaptive Team
The post Announcement — Introducing the New and Improved Idaptive UI appeared first on Security Boulevard.
The post Announcement — Introducing the New and Improved Idaptive UI first appeared on Malware Devil.
https://box2142.temp.domains/~malware7/2020/09/01/announcement-introducing-the-new-and-improved-idaptive-ui/?utm_source=rss&utm_medium=rss&utm_campaign=announcement-introducing-the-new-and-improved-idaptive-ui















 A data leak containing 54,000 scanned New South Wales (NSW) driver’s licenses and various tolling notice statutory declarations were discovered by security researcher Bob Diachenko last week. “More than 50K scanned driver licenses (front+back) and toll notices exposed in a misconfigured S3 bucket. Most likely – part of NSW RMS infrastructure (Road and Maritime, New […]
A data leak containing 54,000 scanned New South Wales (NSW) driver’s licenses and various tolling notice statutory declarations were discovered by security researcher Bob Diachenko last week. “More than 50K scanned driver licenses (front+back) and toll notices exposed in a misconfigured S3 bucket. Most likely – part of NSW RMS infrastructure (Road and Maritime, New […]