
A phone call to an Internet provider in Oregon on Sunday evening was all it took to briefly sideline multiple websites related to 8chan/8kun — a controversial online image board linked to several mass shootings — and QAnon, the far-right conspiracy theory which holds that a cabal of Satanic pedophiles is running a global child sex-trafficking ring and plotting against President Donald Trump. Following a brief disruption, the sites have come back online with the help of an Internet company based in St. Petersburg, Russia.
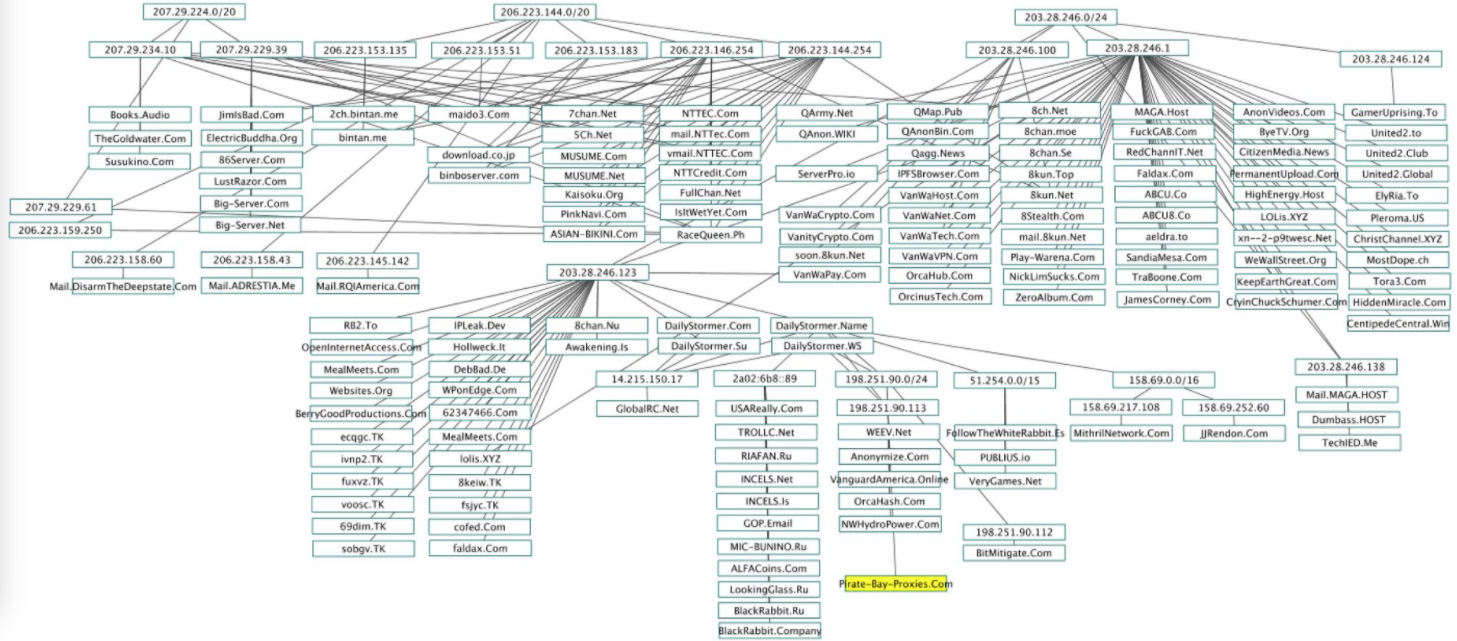
The IP address range in the upper-right portion of this map of QAnon and 8kun-related sites — 203.28.246.0/24 — is assigned to VanwaTech and briefly went offline this evening. Source: twitter.com/Redrum_of_Crows.
A large number of 8kun and QAnon-related sites (see map above) are connected to the Web via a single Internet provider in Vancouver, Wash. called VanwaTech (a.k.a. “OrcaTech“). Previous appeals to VanwaTech to disconnect these sites have fallen on deaf ears, as the company’s owner Nick Lim reportedly has been working with 8kun’s administrators to keep the sites online in the name of protecting free speech.
But VanwaTech also had a single point of failure on its end: The swath of Internet addresses serving the various 8kun/QAnon sites were being protected from otherwise crippling and incessant distributed-denial-of-service (DDoS) attacks by Hillsboro, Ore. based CNServers LLC.
On Sunday evening, security researcher Ron Guilmette placed a phone call to CNServers’ owner, who professed to be shocked by revelations that his company was helping QAnon and 8kun keep the lights on.
Within minutes of that call, CNServers told its customer — Spartan Host Ltd., which is registered in Belfast, Northern Ireland — that it would no longer be providing DDoS protection for the set of 254 Internet addresses that Spartan Host was routing on behalf of VanwaTech.
Contacted by KrebsOnSecurity, the person who answered the phone at CNServers asked not to be named in this story for fear of possible reprisals from the 8kun/QAnon crowd. But they confirmed that CNServers had indeed terminated its service with Spartan Host. That person added they weren’t a fan of either 8kun or QAnon, and said they would not self-describe as a Trump supporter.
CNServers said that shortly after it withdrew its DDoS protection services, Spartan Host changed its settings so that VanwaTech’s Internet addresses were protected from attacks by ddos-guard[.]net, a company based in St. Petersburg, Russia.
Spartan Host’s founder, 25-year-old Ryan McCully, confirmed CNServers’ report. McCully declined to say for how long VanwaTech had been a customer, or whether Spartan Host had experienced any attacks as a result of CNServers’ action.
McCully said while he personally doesn’t subscribe to the beliefs espoused by QAnon or 8kun, he intends to keep VanwaTech as a customer going forward.
“We follow the ‘law of the land’ when deciding what we allow to be hosted with us, with some exceptions to things that may cause resource issues etc.,” McCully said in a conversation over instant message. “Just because we host something, it doesn’t say anything about we do and don’t support, our opinions don’t come into hosted content decisions.”
But according to Guilmette, Spartan Host’s relationship with VanwaTech wasn’t widely known previously because Spartan Host had set up what’s known as a “private peering” agreement with VanwaTech. That is to say, the two companies had a confidential business arrangement by which their mutual connections were not explicitly stated or obvious to other Internet providers on the global Internet.
Guilmette said private peering relationships often play a significant role in a good deal of behind-the-scenes-mischief when the parties involved do not want anyone else to know about their relationship.
“These arrangements are business agreements that are confidential between two parties, and no one knows about them, unless you start asking questions,” Guilmette said. “It certainly appears that a private peering arrangement was used in this instance in order to hide the direct involvement of Spartan Host in providing connectivity to VanwaTech and thus to 8kun. Perhaps Mr. McCully was not eager to have his involvement known.”
8chan, which rebranded last year as 8kun, has been linked to white supremacism, neo-Nazism, antisemitism, multiple mass shootings, and is known for hosting child pornography. After three mass shootings in 2019 revealed the perpetrators had spread their manifestos on 8chan and even streamed their killings live there, 8chan was ostracized by one Internet provider after another.
The FBI last year identified QAnon as a potential domestic terror threat, noting that some of its followers have been linked to violent incidents motivated by fringe beliefs.
Further reading:
What Is QAnon?
QAnon: A Timeline of Violent Linked to the Conspiracy Theory
Read More
The post QAnon/8Chan Sites Briefly Knocked Offline appeared first on Malware Devil.
https://malwaredevil.com/2020/10/19/qanon-8chan-sites-briefly-knocked-offline/?utm_source=rss&utm_medium=rss&utm_campaign=qanon-8chan-sites-briefly-knocked-offline














 2020 has been rife with cyberattacks, but who is behind these hacks? We dig into the details.
2020 has been rife with cyberattacks, but who is behind these hacks? We dig into the details.





