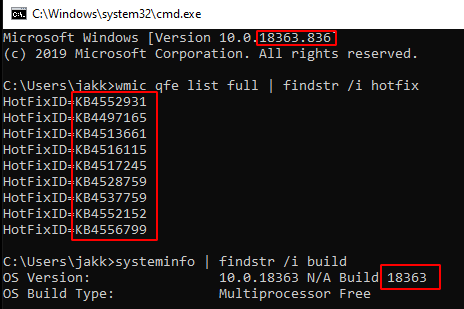
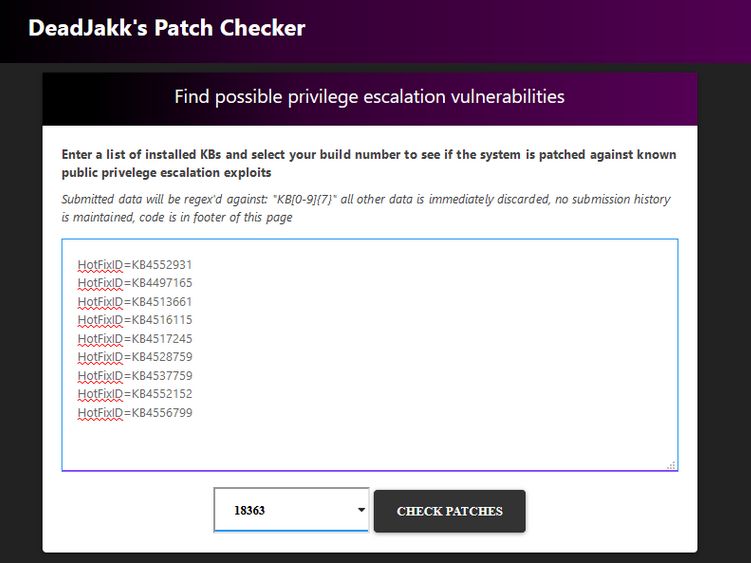
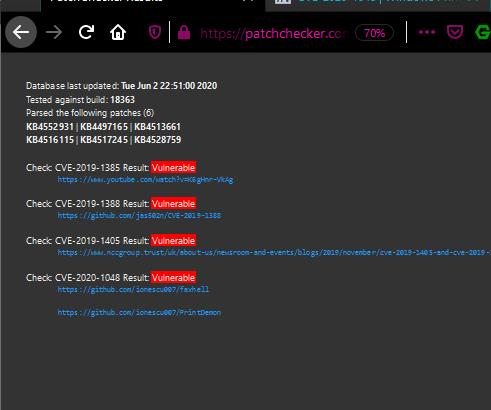
In the past year, Maze ransomware has become one of the most notorious malware families threatening businesses and large organizations. Dozens of organizations have fallen victim to this vile malware, including LG, Southwire, and the City of Pensacola.
The history of this ransomware began in the first half of 2019, and back then it didn’t have any distinct branding – the ransom note included the title “0010 System Failure 0010”, and it was referenced by researchers simply as ‘ChaCha ransomware’.

Ransom note of an early version of Maze/ChaCha ransomware
Shortly afterwards, new versions of this Trojan started calling themselves Maze and using a relevantly named website for the victims instead of the generic email address shown in the screenshot above.

Website used by a recent version of Maze ransomware
Infection scenarios
Mass campaigns
The distribution tactic of the Maze ransomware initially involved infections via exploit kits (namely, Fallout EK and Spelevo EK), as well as via spam with malicious attachments. Below is an example of one of these malicious spam messages containing an MS Word document with a macro that’s intended to download the Maze ransomware payload.

If the recipient opens the attached document, they will be prompted to enable editing mode and then enable the content. If they fall for it, the malicious macro contained inside the document will execute, which in turn will result in the victim’s PC being infected with Maze ransomware.

Tailored approach
In addition to these typical infection vectors, the threat actors behind Maze ransomware started targeting corporations and municipal organizations in order to maximize the amount of money extorted.
The initial compromise mechanism and subsequent tactics vary. Some incidents involved spear-phishing campaigns that installed Cobalt Strike RAT, while in other cases the network breach was the result of exploiting a vulnerable internet-facing service (e.g. Citrix ADC/Netscaler or Pulse Secure VPN). Weak RDP credentials on machines accessible from the internet also pose a threat as the operators of Maze may use this flaw as well.
Privilege escalation, reconnaissance and lateral movement tactics also tend to differ from case to case. During these stages, the use of the following tools has been observed: mimikatz, procdump, Cobalt Strike, Advanced IP Scanner, Bloodhound, PowerSploit, and others.
During these intermediate stages, the threat actors attempt to identify valuable data stored on the servers and workstations in the compromised network. They will then exfiltrate the victim’s confidential files in order to leverage them when negotiating the size of the ransom.
At the final stage of the intrusion, the malicious operators will install the Maze ransomware executable onto all the machines they can access. This results in the encryption of the victim’s valuable data and finalizes the attack.
Data leaks/doxing
Maze ransomware was one of the first ransomware families that threatened to leak the victims’ confidential data if they refused to cooperate.
In fact, this made Maze something of a trendsetter because this approach turned out to be so lucrative for the criminals that it’s now become standard for several notorious ransomware gangs, including REvil/Sodinokibi, DoppelPaymer, JSWorm/Nemty/Nefilim, RagnarLocker, and Snatch.
The authors of the Maze ransomware maintain a website where they list their recent victims and publish a partial or a full dump of the documents they have managed to exfiltrate following a network compromise.

Website with leaked data published by Maze operators
Ransomware cartel
In June 2020, the criminals behind Maze teamed up with two other threat actor groups, LockBit and RagnarLocker, essentially forming a ‘ransomware cartel’. The data stolen by these groups now gets published on the blog maintained by the Maze operators.
It wasn’t just the hosting of exfiltrated documents where the criminals pooled their efforts – apparently they are also sharing their expertise. Maze now uses execution techniques that were previously only used by RagnarLocker.
Brief technical overview
The Maze ransomware is typically distributed as a PE binary (EXE or DLL depending on the specific scenario) which is developed in C/C++ and obfuscated by a custom protector. It employs various tricks to hinder static analysis, including dynamic API function imports, control flow obfuscation using conditional jumps, replacing RET with JMP dword ptr [esp-4], replacing CALL with PUSH + JMP, and several other techniques.
To counter dynamic analysis, this Trojan will also terminate processes typically used by researchers, e.g. procmon, procexp, ida, x32dbg, etc.
The cryptographic scheme used by Maze consists of several levels:
- To encrypt the content of the victim’s files, the Trojan securely generates unique keys and nonce values to use with the ChaCha stream cipher;
- The ChaCha keys and nonce values are encrypted by a session public RSA-2048 key which is generated when the malware is launched;
- The session private RSA-2048 key is encrypted by the master public RSA-2048 key hardcoded in the Trojan’s body.
This scheme is a variation of a more or less typical approach used by developers of modern ransomware. It allows the operators to keep their master private RSA key secret when selling decryptors for each individual victim, and it also ensures that a decryptor purchased by one victim won’t help others.
When executing on a machine, Maze ransomware will also attempt to determine what kind of PC it has infected. It tries to distinguish between different types of system (‘backup server’, ‘domain controller’, ‘standalone server’, etc.). Using this information in the ransom note, the Trojan aims to further scare the victims into thinking that the criminals know everything about the affected network.

Strings that Maze uses to generate the ransom note

Fragment of the procedure that generates the ransom note
How to avoid and prevent
Ransomware is evolving day by day, meaning a reactive approach to avoid and prevent infection is not profitable. The best defense against ransomware is proactive prevention because often it is too late to recover data once they have been encrypted.
There are a number of recommendations that may help prevent attacks like these:
- Keep your OS and applications patched and up to date.
- Train all employees on cybersecurity best practices.
- Only use secure technology for remote connection in a company local network.
- Use endpoint security with behavior detection and automatic file rollback, such asKaspersky Endpoint Security for Business.
- Use the latest threat intelligence information to detect an attack quickly, understand what countermeasures are useful, and prevent it from spreading.
Detection
Kaspersky products protect against this ransomware, detecting it as Trojan-Ransom.Win32.Maze; it is blocked by Behavior-based Protection as PDM:Trojan.Win32.Generic.
We safeguard our customers with the best Ransomware Protection technologies.

TIP Cloud Sandbox report summary and execution map with mapping on MITRE ATT&CK Framework
IOCs
2332f770b014f21bcc63c7bee50d543a
CE3A5898E2B2933FD5216B27FCEACAD0
54C9A5FC6149007E9B727FCCCDAFBBD4
8AFC9F287EF0F3495B259E497B30F39E
The post Life of Maze ransomware appeared first on Malware Devil.
https://malwaredevil.com/2020/10/21/life-of-maze-ransomware/?utm_source=rss&utm_medium=rss&utm_campaign=life-of-maze-ransomware