© 2020 Bob Carver, CISM, CISSP, M.S.
Very few people predicted a pandemic in 2020 which would turn our economy and work force on its head. Where working from home was to become the norm and working in the office was the exception. In many cases the acceleration of remote education, the streaming of movies, web conferences and whatever you can afford to be delivered to your front door followed the same trend.
As the pandemic continued to intensify, the largest Nation-State supply chain compromise of SolarWinds took place. This created cyber havoc in at least 18,000 of their business and government customers. More recently we have heard that Microsoft was breached and some source code was accessed. This could create issues for a user footprint on a global scale.
The cloud had already made great advances in market share taking away processing power from traditional data centers. Because of the pandemic, most data center personnel are not working on location to roll out new bare metal servers to keep up with increased processing demand. As a result, more projects were put in the cloud.
This past year the castle and moat network architecture and bare metal servers of traditional data centers continued to be pushed further away and made a relic of the past. In normal times, this digital transformation could have taken another 5 or more years.

PREDICTIONS
Securing the Supply Chain Will Finally Become a High Priority
Compared to SolarWinds eventual costs to remediate, NotPetya was relatively small change (estimated over $1 billion in costs.) When Merck and others attempted to collect on their cybersecurity policy, the insurers declared it an “act of war” which was a type of event that was not included in their insurance coverage. Now with the recent announcement of Microsoft being compromised and source code accessed, even the SolarWinds breach could look relatively minor by comparison.
Historically, there was a time where updates to computers, network devices and the like were manually put in place only after checking the file you downloaded matched a checksum (ensuring the update code had not been maliciously modified.) We have become used to updating systems and simply trusting the code that is fed to us from our vendors. Of course in that method, the posted checksums could be maliciously modified.
Securing these updates and other parts of the supply chain will need to go through a revolution. Some may suggest that these updates be secured by blockchain technology, but native blockchain is not secure by itself.
It will have to be hardened to acceptably secure standards where it cannot be modified by outside parties.
Cybersecurity Insurance Policies May Not Cover What You Think They Cover
In this age of massive breaches when you go to collect, you end up with little or no payout from the insurance companies. NotPetya was an excellent example when insurance companies used the “Force Majeure” card when it came to compromised corporations attempting to collect on their insurance policies. Merck ($310 million), Maersk ($300 million) and FedEx ($300 million) were just a few companies stuck with a large portion of the bill to recover from this attack.
Since the SolarWinds cyberattack was thought to be a result of a large Nation-State cyberattack, it is likely that insurance companies will treat it the same way as the NotPetya cyberattacks.
In the meantime, larger corporations and those that can afford it must allocate funds for incidents for similar breaches in the future just in case they are not deemed an insurable event.
Good Enough Security is Not Nearly Good Enough
- Small to Medium Size Businesses
At least half of the businesses that are currently in existence have no business attempting to do their own security. These businesses either cannot afford seasoned cybersecurity personnel or are not able to locate someone with the appropriate experience to manage a semblance of a security risk management program.
Quite often cybercriminals will utilize ransomware and will blackmail business owners for exfiltrated sensitive data. There are others that will access bank accounts or manipulate bank transfers bypassing normal security controls. This will cause a serious disruption of normal business operations and result in 60% of these businesses going under. These businesses should consider hiring a (Managed Detection and Response) MDR service.
I have not met any security professionals that have admitted saying, “We have all of the security personnel, budgets and security tools we need and want to defend our business against any and all cyberattacks.” After NotPetya and SolarWinds cyberattacks, it has become obvious that there have been vulnerabilities internally and externally that were not foreseen. Additionally, it may take a large portion of 2021 to know the full extent of the damage from these recent cyberattacks. We may discover many other organizations have been touched in some way by these attacks.
Questions to Ask Yourself:
- Have you tightened your security since the amount of remote work has increased?
- Do you have all the logs you need in case of a compromise?
- Do you have visibility and context to what events are happening on your computers and traversing your networks?
- Have you benchmarked your security and incident response team against others in your industry?
- If you have participated in benchmarking your business, do you have an idea of where you can improve?
Having a Breach Will Have Consequences
For the longest time, corporate and government breaches resulted in (1) a slap on the hand, a fine that was a very small percentage of annual revenue and (2) giving consumers that had their personal information exposed, one year of credit monitoring. That may all be about to change.
Already SolarWinds is being evaluated for a Moody’s credit downgrade, making it more difficult to borrow and raise money for business operations. We have yet to know how many lawsuits will result in this supply chain compromise. This is because we don’t know the time and money that will be lost in restoring and verifying hundreds of thousands of systems for compromise.
Ransomware
This is not going away anytime soon. There is still too much money to be made.
For small enterprises with an average of 50 employees, the typical ransomware incident cost the company $73,000. They will need effective methods of endpoint security, backups and business continuity to minimize this risk.
For larger enterprises, the average breach cost was approximately $4 million dollars according to IBM. In the ForgeRock Consumer Identity Breach Report in 2020, they reported more than 5 billion records that were compromised in 2019 and those breaches cost U.S. organizations more than $1.2 trillion.
The latest trend in cybercrime is to steal your valuable sensitive data first, then encrypt your hard drives making them unusable. If you have good backups and you can fully restore without any malware then the criminal’s “Plan B” is to blackmail you by threatening to release all of your sensitive data.
The next escalations may involve firmware and IoT devices, possibly even bricking devices if the ransom is not paid.
Continued Expansion of AI, Machine Learning and Deep Learning to Detect Cyberattacks
There needs to be continued use and advancement in these detection and mitigation mechanisms; but like any other methodology, these methods by themselves are not a silver bullet to solve all of our cyberattacks. They are simply tools in the toolbelt that can be utilized for great good.
The difficultly is that these technologies do not like ambivalence or gray areas. They like well-defined boundaries of good or bad. Cybercriminals and Nation States will craft many of their attacks to look like normal traffic, normal processes and will perhaps add additional flows and processes to set a “normal baseline” to throw these detection mechanisms off of the trail.
Zero Trust
Zero Trust is not a single technology, it is a framework that was developed by Forrester Research in 2010. It takes the stance of “Do Not Trust and Verify.” This includes the utilization of technologies like IAM (Identity Access Management), MFA (Multi Factor Authentication), micro segmentation of networks and cloud platforms, verifying the identity of who is attempting to access a network, cloud or application and limiting how and what assets users are able to access along with the level of permissions granted. Enabling this framework in a secure manner will continue to be more important than ever. Those that implement Zero Trust well will reduce their risk substantially.
More Wolves in Sheep Clothing

- Known Good Software Going Bad
Caveat Emptor, be careful of what software is downloaded to your computers. This has been going on for some time. The software that starts out clean is recognized with a legitimate golden digital certificate and not recognized as malicious by all major endpoint security products. Give it time, then a backdoor starts updating the original software without any warning or any user acknowledgement or interaction. Next you have keyloggers, password crackers, enumeration, network discovery tools along with multiple layers of malware and APT’s for a backup plan to stay embedded on your computers and within your network.
Sometimes this malicious update starts within hours, other times I have seen sleep cycles in application code where the malware downloads did not start until six months after installation.
Know your software and suppliers you can trust. Be careful downloading free or inexpensive software that has the potential to become the malicious gift that keeps on giving.
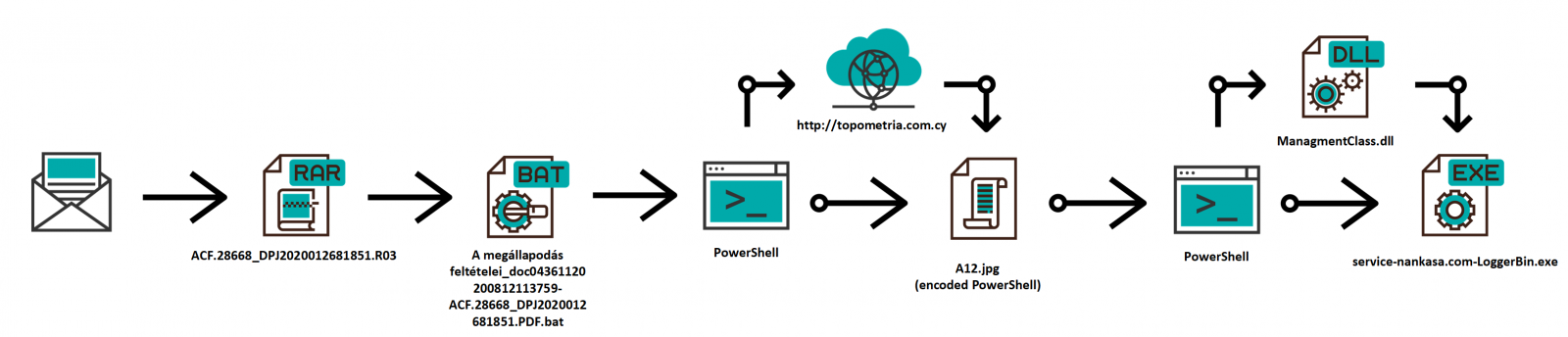
- Supply Chain-Based Cyberattacks
What is the next level of cyberattacks that are utilizing the methodology of Wolf in Sheep’s Clothing? It is poisoning the supply chain. I am surprised we hadn’t seen this earlier. We have seen where nation-state attacks utilized NotPetya and SolarWinds by poisoning a single entity to compromise many. Even recently, we saw Microsoft being breached and have yet to know the full extent of the damage.
Third Party Risk and Governance
As a result of recent supply chain compromises, management of third party risk will be more important than ever. Simple checkbox questionnaires self-assessing “Do you do this?”, “Do you have one of these?” will no longer be sufficient. A more rigorous method of measuring level of the security that is in place will be needed and will eventually require a formal third party verification.
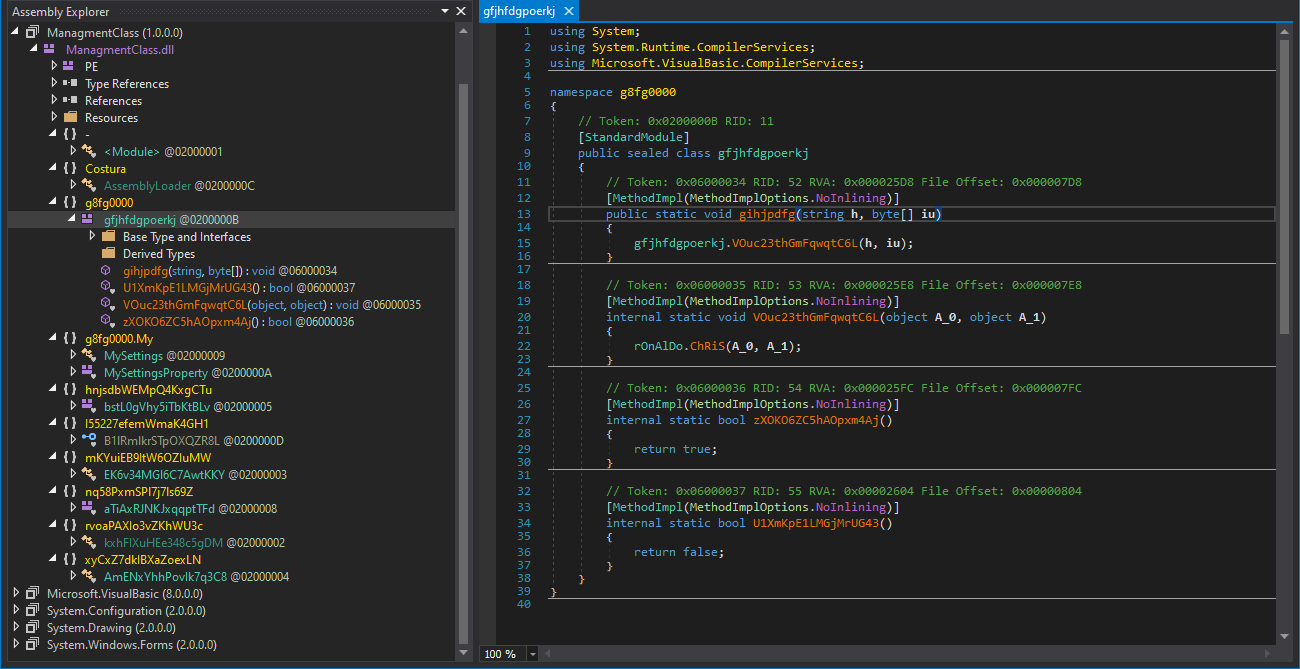
Fileless Malware, Living Off of the Land, Process Hollowing, Process Masquerading and Processes That Run in Memory
These are more difficult to analyze unless you have access to full context and all related data flows, processes (whether on memory or on disk) and decryption of TLS or methods of obfuscation.
We will continue to see a larger percentage of cyberattacks utilizing these types of TTPs. Traditional malware analysis of files may be needed less often and logging misuse of WMI, Powershell and other legitimate software applications used in a malicious manner.
The CISO Gets Some Help, Especially in Larger Organizations
We will start to see more positions of Chief Data Officer and/or Chief Privacy Officer in larger organizations. The job of securing, data, privacy, networks and, in some cases, even physical security is simply too large a job for a single person in the largest corporations.
Wish List
IoT Security Bill
This was on my previous wishlist. Baby steps. This is sometimes how real life is, you don’t get everything you want all at once. Progress was made when Washington, D.C. passed a bill on IoT Security. Does it have any stipulations on who takes responsibility? That is unclear. It appears to point to a NIST document for IoT guidelines. Perhaps folks in U.S. government will have to attempt to follow those guidelines in purchasing new IoT devices? Does the IoT bill layout who is responsible when things go wrong? I don’t think there will be any changes until billions or more dollars are lost due to mayhem of compromised IoT devices interrupting commerce and peoples’ connectivity to our new normal remote work routines. Mirai and Reaper botnets have already shown us what damage they can do. This is not in the theoretical realm anymore. I am not looking to point fingers. I am looking for a game plan (Risk Management and an Incident Response Plan) where we know who will be required to get involved and take responsibility when the SHTF
Cybersecurity Education
This was on my previous wish list. Progress is being made. Commercial organizations, Girl Scouts, Women’s Empowerment organizations and Charter Schools are being put in place to teach cybersecurity in middle school and high school. Kudos! We are just getting started. Let’s get them to start learning in grade school. Let’s keep up the momentum. There is much more to do.
Understand Compliance Does Not Equal a Secure Risk Management Program.
Congratulations to those that rank high in NIST CSF, various ISO frameworks and the like. You probably are better off than many other companies. However, there are many vulnerabilities that have yet to be discovered and Tools, Techniques and Procedures utilized in cyberattacks that we have yet to experience where we have no good method of detection or mitigation.
Just because you scored well doesn’t mean the next cyberattack won’t catch you with your pants down. Think SolarWinds, Eternal Blue and others.
That is why I commend the continuous monitoring and continuous improvement frameworks because this work is never complete and you can’t rest on your laurels.
Stop Utilizing RDP and Other Pseudo Secure Web Methods of Login When Exposed to the Internet
These are high on the list of why businesses get compromised. Please find more secure ways to login to assets on public IP addresses.
Everyone Start Utilizing 2FA (2 Factor Authentication) Wherever it is Available
Do you want to lower the risk of a compromised account substantially this year? Review all of your website and application login accounts starting with email and financial accounts. Verify that you have 2FA or MFA (Two Factor or Multi-Factor Authentication in place.) Attempt to avoid SMS text and utilize out-of-band apps or, in more critical situations, proven security keys.
Originally posted at: https://www.linkedin.com/pulse/cybersecurity-predictions-wish-list-2021-carver-cism-cissp-ms-/
About the Author

Bob Carver, CISM, CISSP, M.S.
I uncover previously unseen cybersecurity risk and creatively architect solutions.
Threat Hunting the security unknowns that escape all traditional security monitoring.
Interrupting malicious traffic.
Previsiously, monitored hundreds of botnets and ten of thousands infected endpoints including PC’s, Smartphones and Apple OS X.
Initially, started, oversaw the first full-time Verizon Wireless Security Incident Response Team and Security Monitoring team.
Previously Architect and acting Project Manager for ArcSight Security monitoring and reporting, processing approximately 20 million of potential security events each day.
Regular contributor to Verizon-wide risk team.
Participate in and initiate changes in network architecture in response to various attacks.
Current Projects: Interrupting Command and Control/Malicious traffic; Security Awareness.
Have had experience from startups to Federal Government to Fortune 500. IT Operations and Network management for a worldwide network.
*CISM (Certified Information Security Manager)
*CISSP (Certified Information Security Professional).
*Passed CBCP Exam (Certified Business Continuity Professional) CBCP candidate
The post Cybersecurity Predictions and a Wish List for 2021 by Bob Carver appeared first on Hakin9 – IT Security Magazine.
Read More
The post Cybersecurity Predictions and a Wish List for 2021 by Bob Carver appeared first on Malware Devil.
https://malwaredevil.com/2021/01/04/cybersecurity-predictions-and-a-wish-list-for-2021-by-bob-carver/?utm_source=rss&utm_medium=rss&utm_campaign=cybersecurity-predictions-and-a-wish-list-for-2021-by-bob-carver