In October 2020, KrebsOnSecurity looked at how a web of sites connected to conspiracy theory movements QAnon and 8chan were being kept online by DDoS-Guard, a dodgy Russian firm that also hosts the official site for the terrorist group Hamas. New research shows DDoS-Guard relies on data centers provided by a U.S.-based publicly traded company, which experts say could be exposed to civil and criminal liabilities as a result of DDoS-Guard’s business with Hamas.
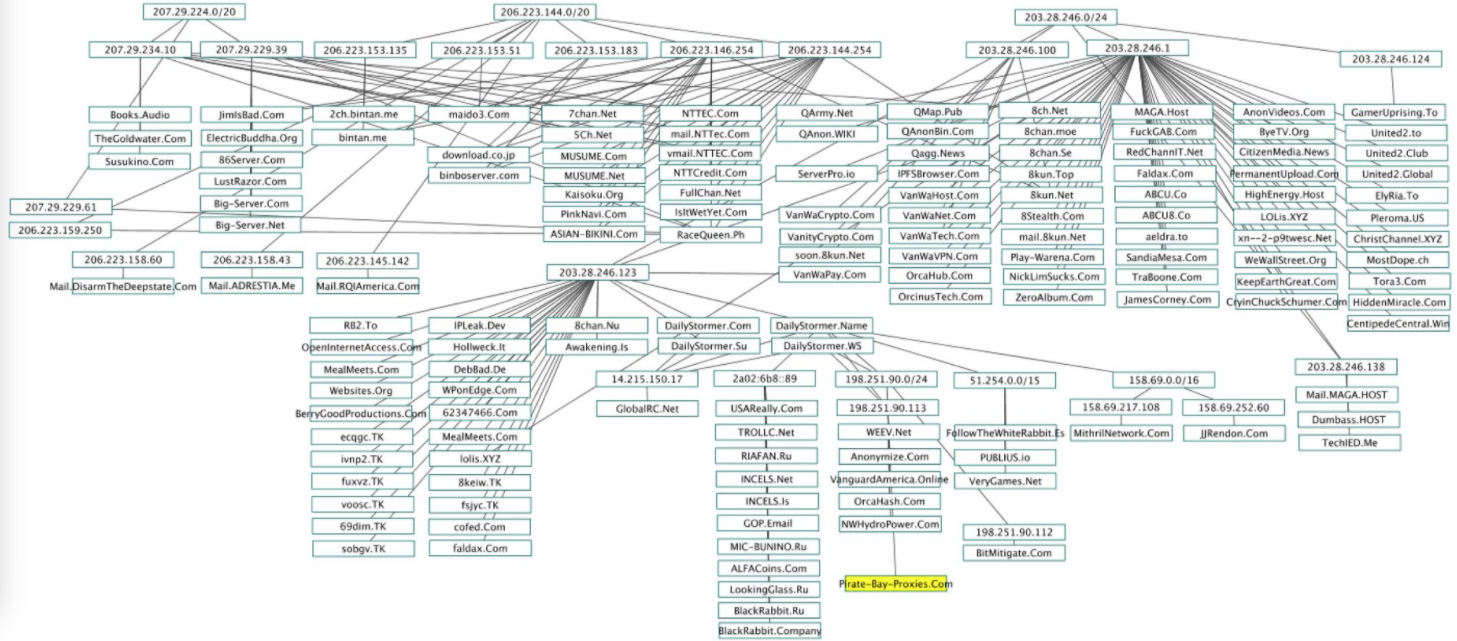
Many of the IP address ranges in in this map of QAnon and 8Chan-related sites — are assigned to VanwaTech. Source: twitter.com/Redrum_of_Crows
Last year’s story examined how a phone call to Oregon-based CNServers was all it took to briefly sideline multiple websites related to 8chan/8kun — a controversial online image board linked to several mass shootings — and QAnon, the far-right conspiracy theory which holds that a cabal of Satanic pedophiles is running a global child sex-trafficking ring and plotting against President Donald Trump.
From that piece:
A large number of 8kun and QAnon-related sites (see map above) are connected to the Web via a single Internet provider in Vancouver, Wash. called VanwaTech (a.k.a. “OrcaTech“). Previous appeals to VanwaTech to disconnect these sites have fallen on deaf ears, as the company’s owner Nick Lim reportedly has been working with 8kun’s administrators to keep the sites online in the name of protecting free speech.
After that story, CNServers and a U.K.-based hosting firm called SpartanHost both cut ties with VanwaTech. Following a brief disconnection, the sites came back online with the help of DDoS-Guard, an Internet company based in Russia. DDoS-Guard is now VanwaTech’s sole connection to the larger Internet.
A review of the several thousand websites hosted by DDoS-Guard is revelatory, as it includes a vast number of phishing sites and domains tied to cybercrime services or forums online.
Replying to requests for comment from a CBSNews reporter following up on my Oct. 2020 story, DDoS-Guard issued a statement saying, “We observe network neutrality and are convinced that any activity not prohibited by law in our country has the right to exist.”
But experts say DDoS-Guard’s business arrangement with a Denver-based publicly traded data center firm could create legal headaches for the latter thanks to the Russian company’s support of Hamas.
In a press release issued in late 2019, DDoS-Guard said its services rely in part on a traffic-scrubbing facility in Los Angeles owned by CoreSite [NYSE:COR], a real estate investment trust which invests in “carrier-neutral data centers and provides colocation and peering services.”
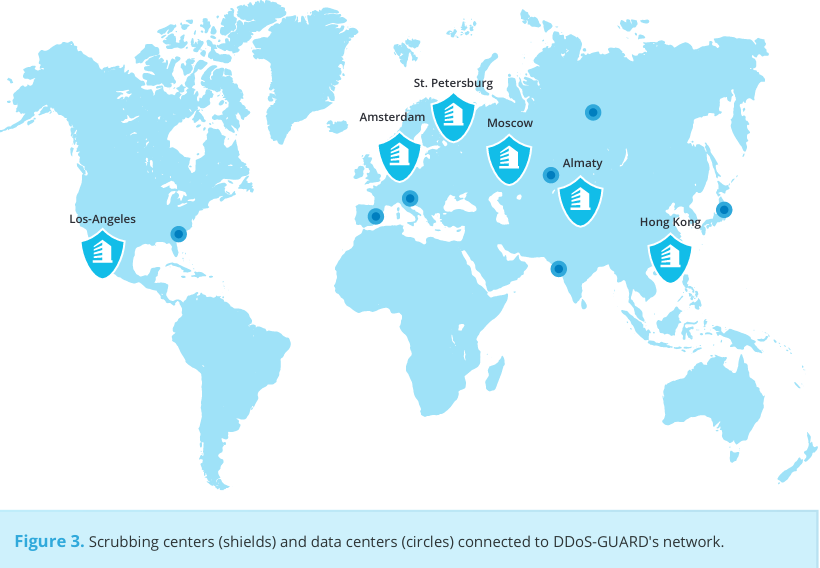
This facilities map published by DDoS-Guard suggests the company’s network actually has at least two points of presence in the United States.
Hamas has long been named by the U.S. Treasury and State departments as a Specially Designated Global Terrorist (SDGT) organization. Under such a designation, any U.S. person or organization that provides money, goods or services to an SDGT entity could face civil and/or criminal prosecution and hefty fines ranging from $250,000 to $1 million per violation.
Sean Buckley, a former Justice Department prosecutor with the law firm Kobre & Kim, said U.S. persons and companies within the United States “are prohibited from any transaction or dealing in property or interests in property blocked pursuant to an entity’s designation as a SDGT, including but not limited to the making or receiving of any contribution of funds, goods, or services to or for the benefit of individuals or entities so designated.”
CoreSite did not respond to multiple requests for comment. But Buckley said companies can incur fines and prosecution for violating SDGT sanctions even when they don’t know that they are doing so.
In 2019, for example, a U.S. based cosmetics company was fined $1 million after investigators determined its eyelash kits were sourcing materials from North Korea, even though the supplier in that case told the cosmetics firm the materials had come from China.
“U.S. persons or companies found to willfully violate these regulations can be subject to criminal penalties under the International Emergency Economic Powers Act,” Buckley said. “However, even in the case that they are unaware they’re violating these regulations, or if the transaction isn’t directly with the sanctioned entity, these companies still run a risk of facing substantial civil and monetary penalties by the Department of Treasury’s Office of Foreign Asset Control if the sanctioned entity stands to benefit from such a transaction.”
DDoS-Guard said its partnership with CoreSite will help its stable of websites load more quickly and reliably for people visiting them from the United States. It is possible that when and if CoreSite decides it’s too risky to continue doing business with DDoS-Guard, sites like those affiliated with Hamas, QAnon and 8Chan may become more difficult to reach.
Meanwhile, DDoS-Guard customer VanwaTech continues to host a slew of sites promoting the conspiracy theory that the U.S. 2020 presidential election was stolen from President Donald Trump via widespread voting fraud and hacked voting machines, including maga[.]host, donaldsarmy[.]us, and donaldwon[.]com.
These sites are being used to help coordinate a protest rally in Washington, D.C. on January 6, 2021, the same day the U.S. Congress is slated to count electoral votes certified by the Electoral College, which in December elected Joseph R. Biden as the 46th president of The United States.
In a tweet late last year, President Trump urged his supporters to attend the Jan. 6 protest, saying the event “will be wild.”
8chan, which has rebranded as 8kun, has been linked to white supremacism, neo-Nazism, antisemitism, multiple mass shootings, and child pornography. The FBI in 2019 identified QAnon as a potential domestic terror threat, noting that some of its followers have been linked to violent incidents motivated by fringe beliefs.
The post Hamas May Be Threat to 8chan, QAnon Online appeared first on Malware Devil.
https://malwaredevil.com/2021/01/05/hamas-may-be-threat-to-8chan-qanon-online/?utm_source=rss&utm_medium=rss&utm_campaign=hamas-may-be-threat-to-8chan-qanon-online