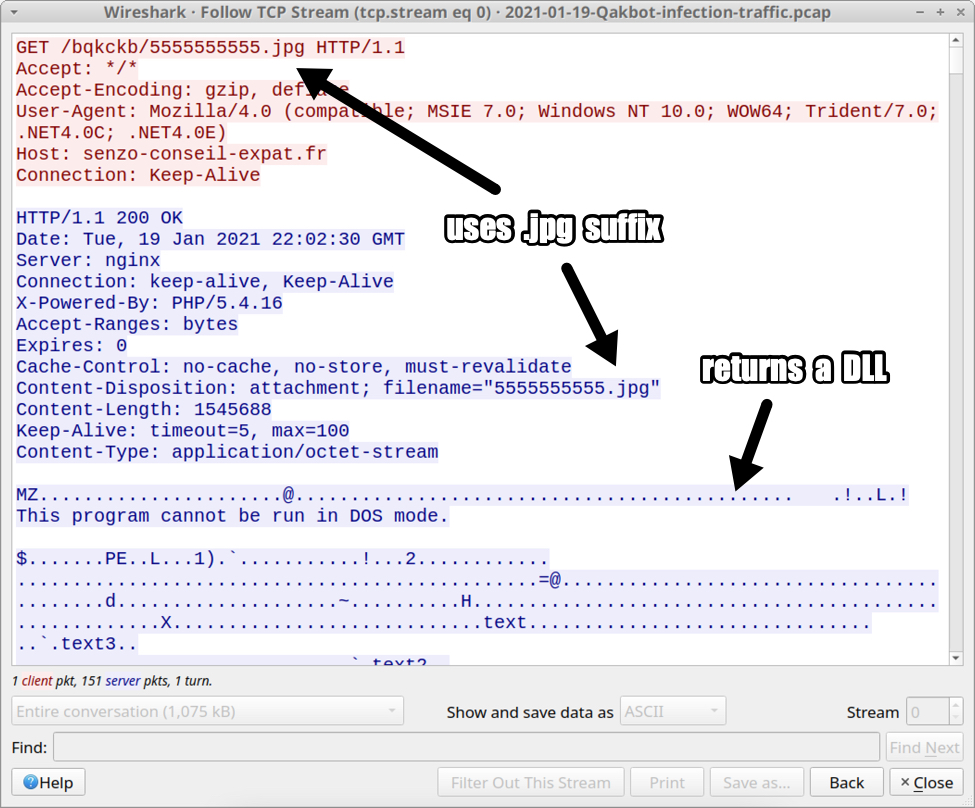
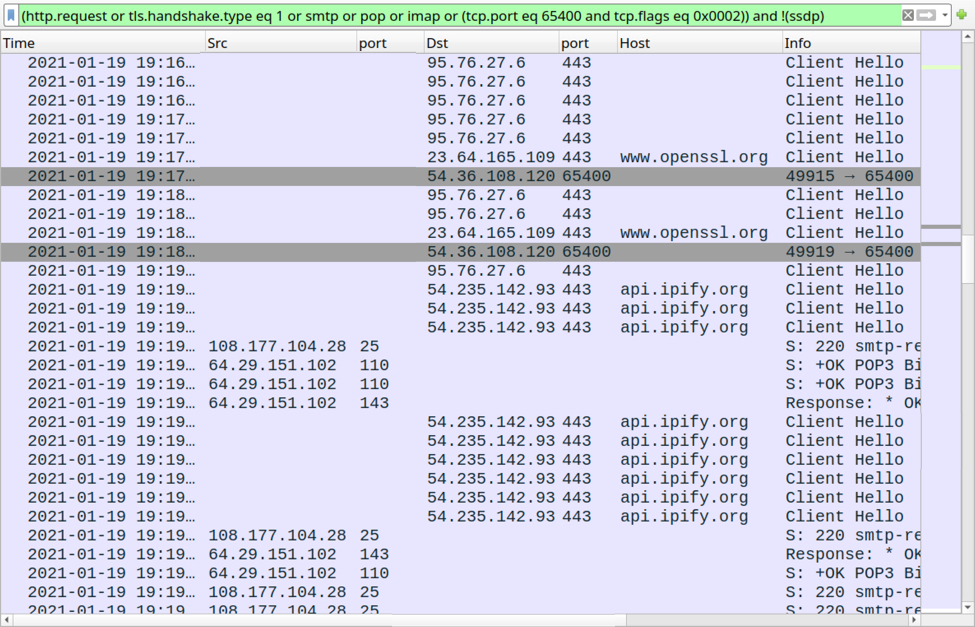
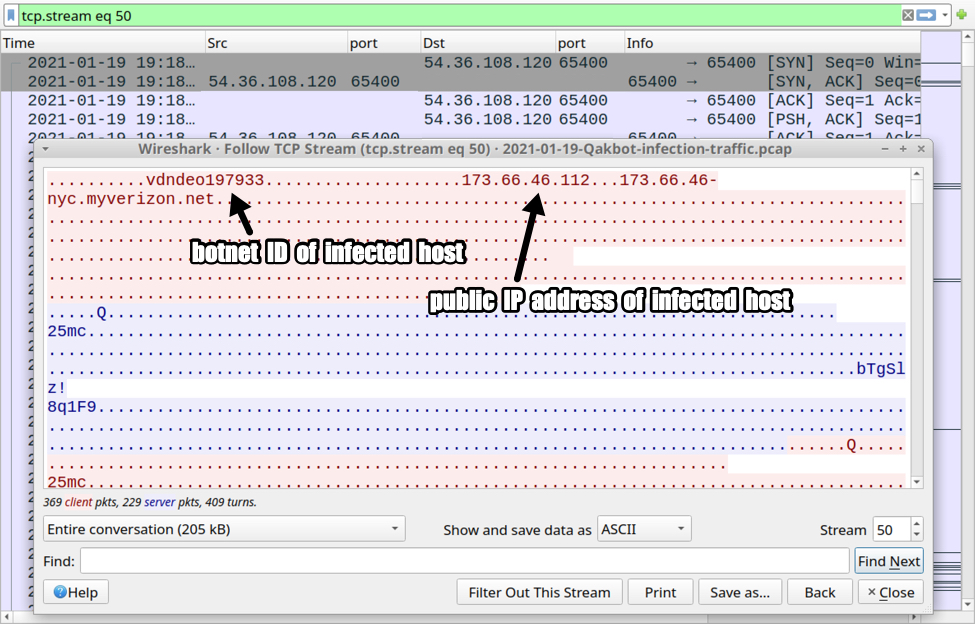
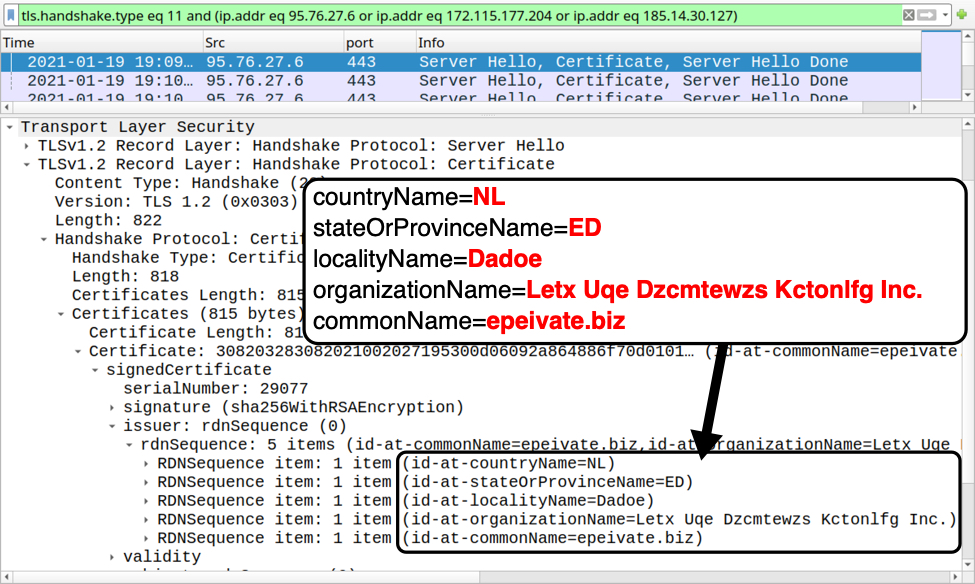
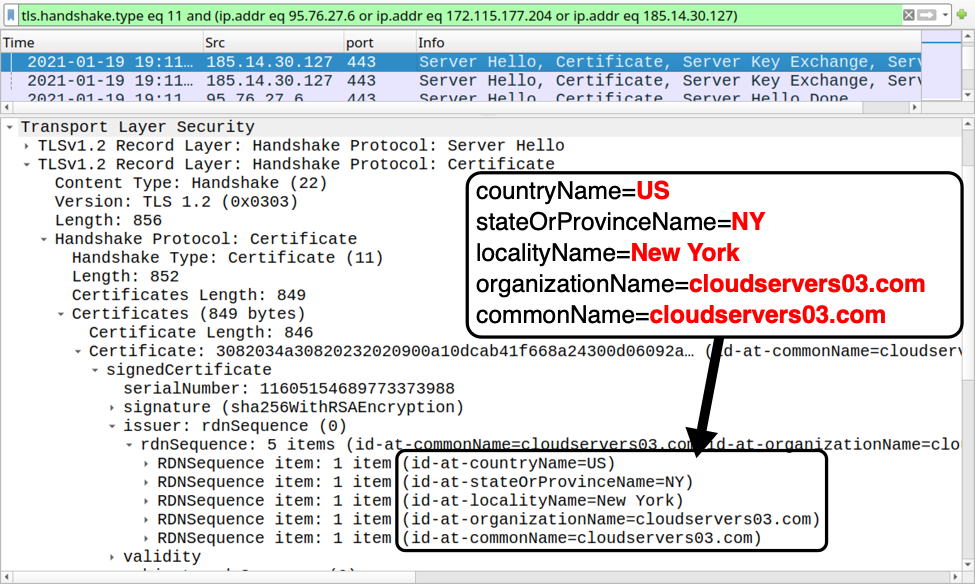
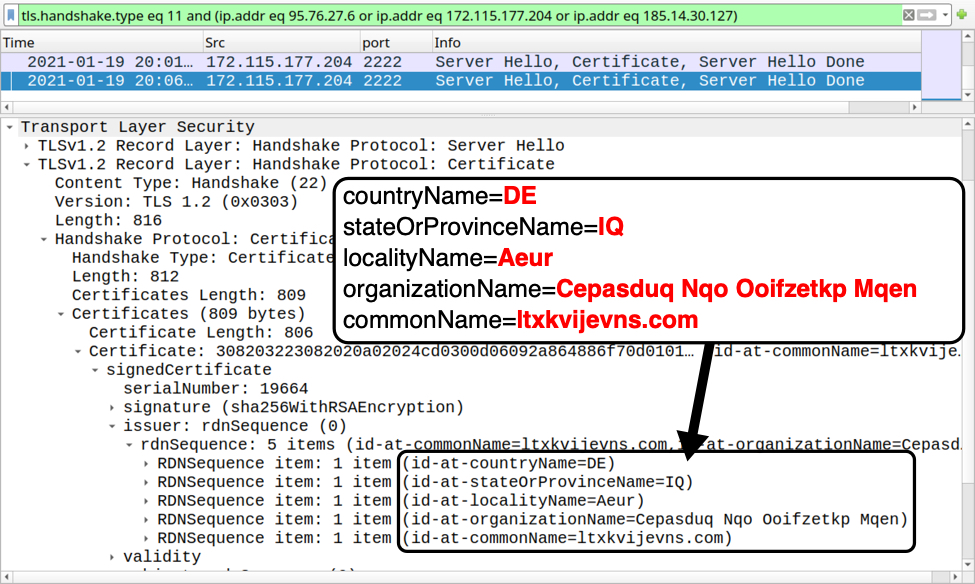
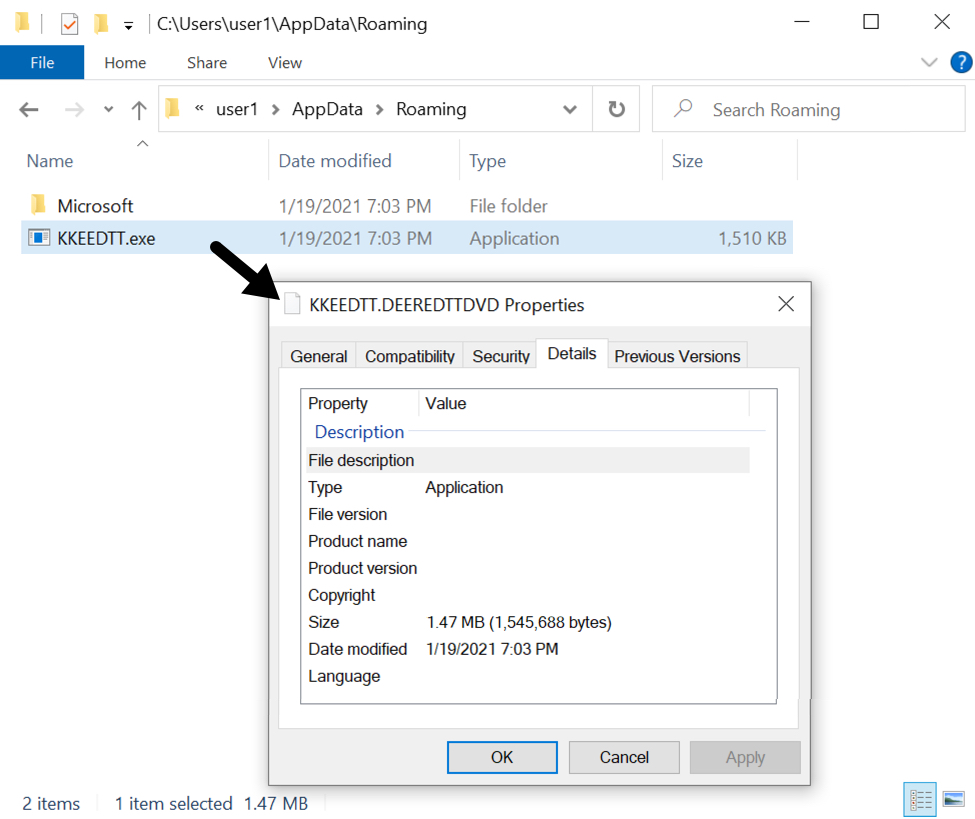
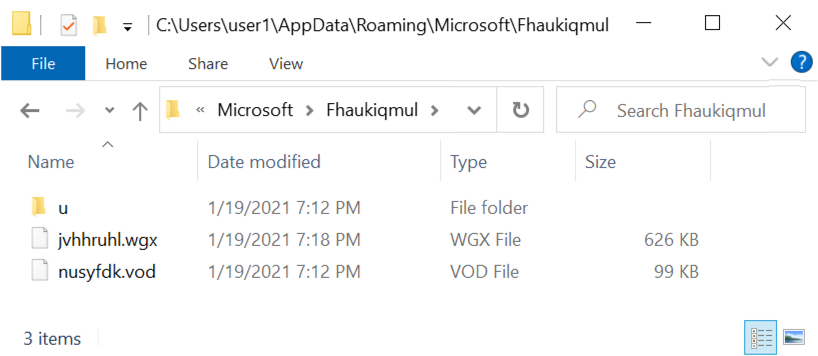
Metadata, which gives background information on pieces of data, is typically hidden. It becomes a problem when accidentally revealed. Often tied to photography mishaps, it can be timestamps. It might be location. In some cases, it can be log analysis. Many tutorials exist to strip this information out. This is because it can reveal more than intended when it hits the public domain. Default settings are often to blame. For example, a mobile photography app or camera may embed GPS data by default.
Some people may find this useful; quite a few more may object to it as a creepy privacy invasion.
Well, that’s metadata. Now you have an idea what kind of things can lurk without knowledge. We can see what happens when we deliberately enable a data / tagging related function.
Watermarking: what’s the deal?
An interesting story has recently emerged on The Intercept, of voluntary data (in the form of watermarks) wrapped into Zoom recordings, which could cause headaches in unexpected ways. Watermarks aren’t hidden—they’re right there by design, if people choose to use them. And the visual side of this data is supposed to be viewable during the call.
The Intercept talks about accidental identity reveals, via data embedded into calls, in relation to the ever-present videoconferencing tool. You’d be forgiven for thinking the identity reveal referenced in the article had something to do with the watermarks, but no.
The reveal happened because someone recorded a video call and dropped it online, with participant’s faces on display. The people involved appear to be at least reasonably well known. The secret identity game was up regardless of what was under the hood.
Cause and effect
What the rest of the article is about, is theorising on the ways embedded metadata could cause issues for participants. Zoom allows for video and audio watermarking, with video of course being visual and so easier to spot. Video displays a portion of a user’s email address when someone is sharing their screen. Audio embeds the information of anyone recording the call into the audio, and Zoom lets you know who shared it. You must ask Zoom to do this, and the clip has to be more than 2 minutes in length.
Essentially, video watermarking is to help you know who is sharing and talking during the call. Audio watermarking is to allow you to figure out if someone is sharing without permission. The Intercept explores ways this could cause problems where confidentiality is a concern.
Some identity caveats
If Zoom content is shared online without permission, it may not matter much if revealing metadata is included, unless the video call is audio only. This is because people can be easy to identify visually. Is a public figure of some sort involved? The game is already lost. If they’re not normally a public facing persona, people could still find them via reverse image search or other matching tools. And if they can’t, a well-known location, or a name-badge, could give them away. There are so many variables at work, only the participants may know for sure.
Hunting the leaker: does it matter?
While the other concern of identifying the leaker is still important, your mileage may vary in terms of how useful it is, versus how much of an inadvertent threat it presents. It’s possible the leaker may not care much if they’re revealed. They may have used a fake identity, or even compromised a legitimate account in order to do the leaking.
It’s also possible that someone with a grudge could leak something then pretend they’d been compromised. If this happened, would you have a way of being able to determine the truth of the matter? Or would you simply take their word for it?
Weighing up the risk
All good questions, and a valuable reminder to consider which videoconferencing tools you want to make use of. For some organisations and individuals, there’s a valid use for the metadata dropped into the files. For others, it might be safer on balance to leave them out. It might even be worth using a virtual background instead of something which reveals personal information. It might be worth asking if you even need video at all, depending on sensitivity of call.
The choice, as always, is yours.
The post Zoom watermarking: pros and cons appeared first on Malwarebytes Labs.
The post Zoom watermarking: pros and cons appeared first on Malware Devil.
https://malwaredevil.com/2021/01/20/zoom-watermarking-pros-and-cons/?utm_source=rss&utm_medium=rss&utm_campaign=zoom-watermarking-pros-and-cons