
Introduction
Late last week, we saw new samples of Word documents from TA551 (Shathak) pushing malware. This actor was active up through 2020-12-18 pushing IcedID malware before going on break for the holidays. Now that it’s returned, TA551 has been pushing Qakbot (Qbot) malware instead of IcedID.
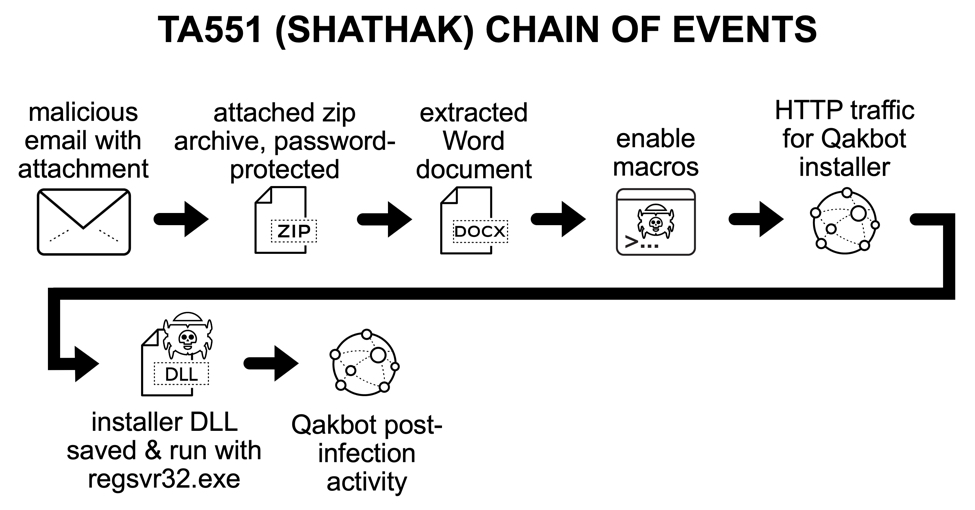
Shown above: flow chart for recent TA551 (Shathak) activity so far in January 2021.
Images from the infection
See below for images associated with the infection in my lab environment.
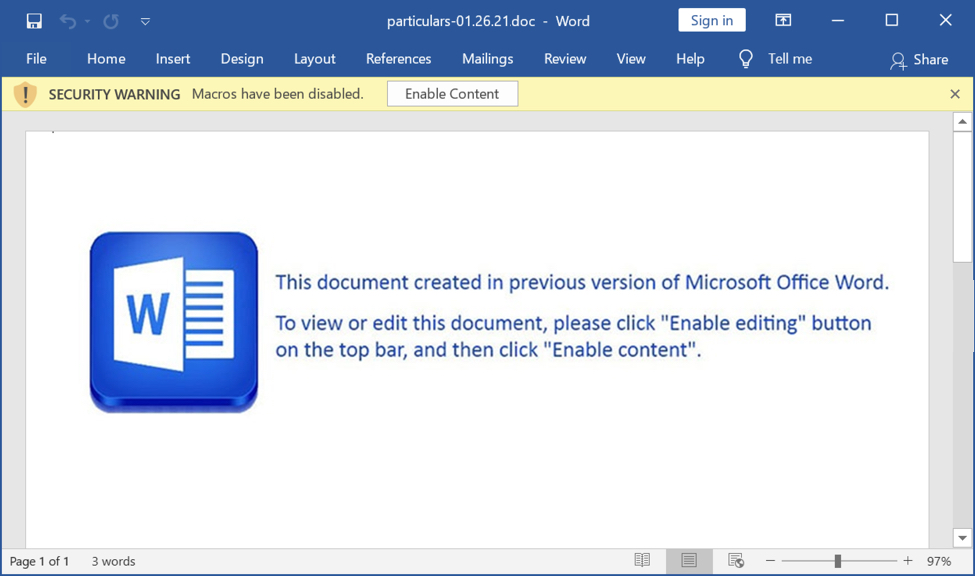
Shown above: Screenshot of the TA551 (Shathak) Word document with macros for Qakbot (Qbot).
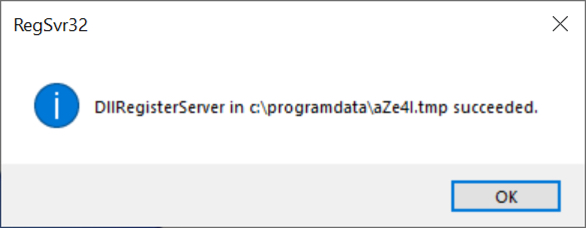
Shown above: Regsvr32 pop up message when the malware DLL to install Qakbot has successuflly run.
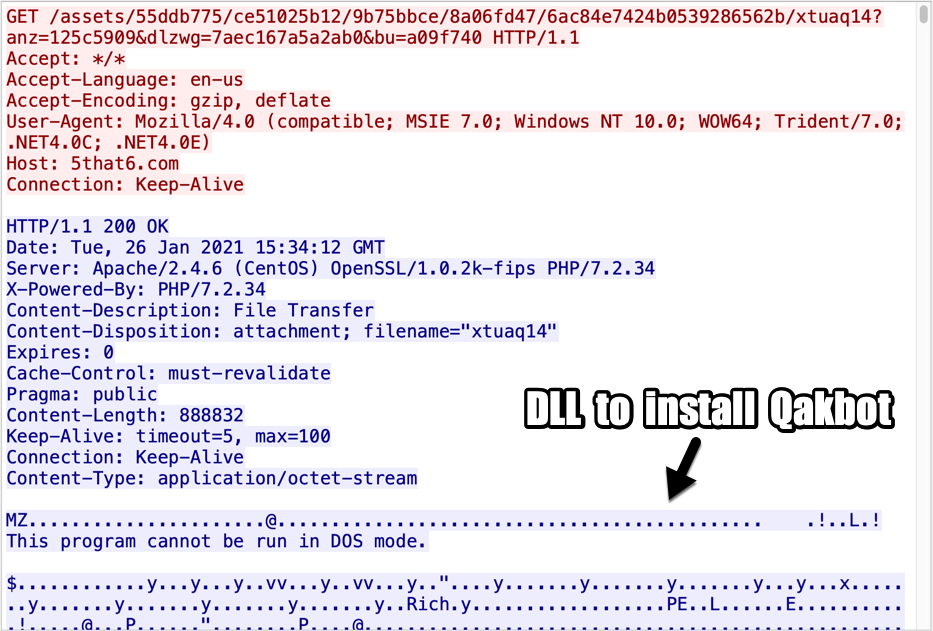
Shown above: Start of TCP stream showing the HTTP request and response for the initial DLL to install Qakbot (Qbot).
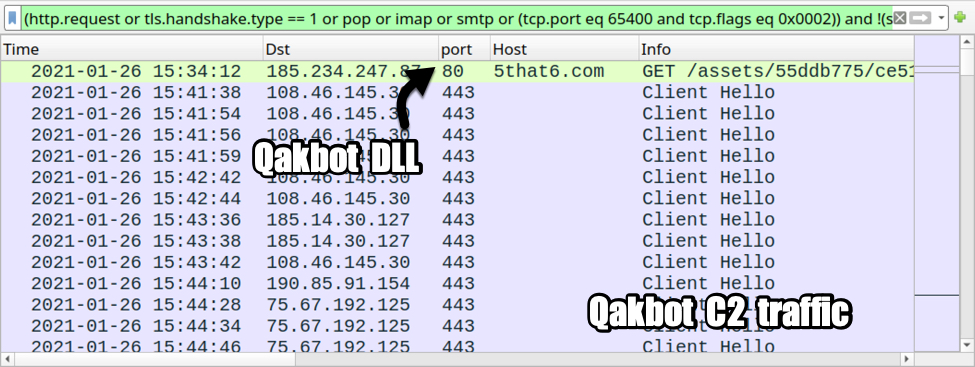
Shown above: Traffic from the infection filtered in Wireshark (part 1).
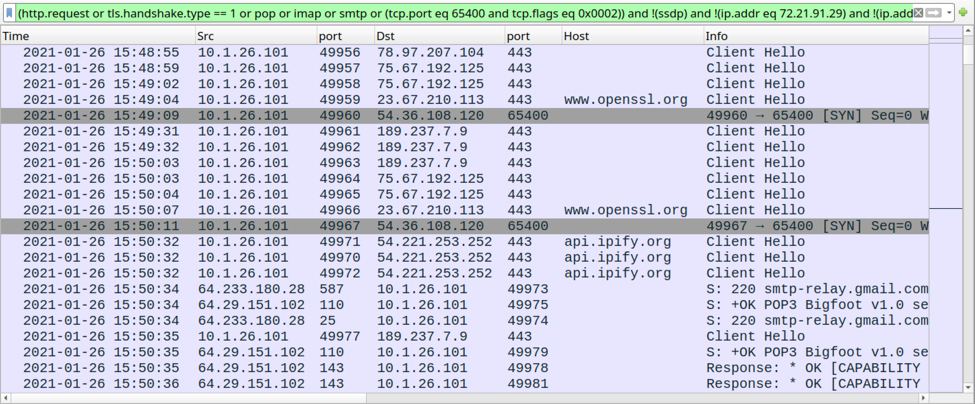
Shown above: Traffic from the infection filtered in Wireshark (part 2).
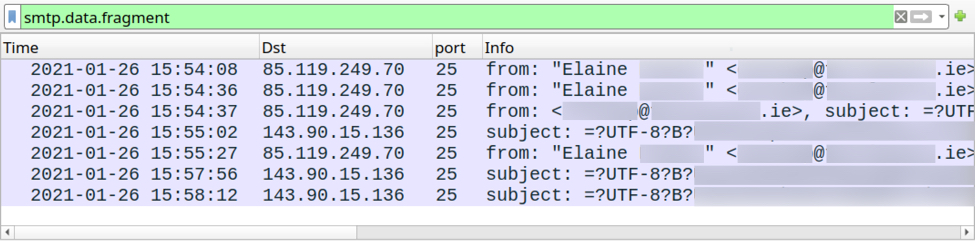
Shown above: Traffic from the infection filtered in Wireshark (part 3).
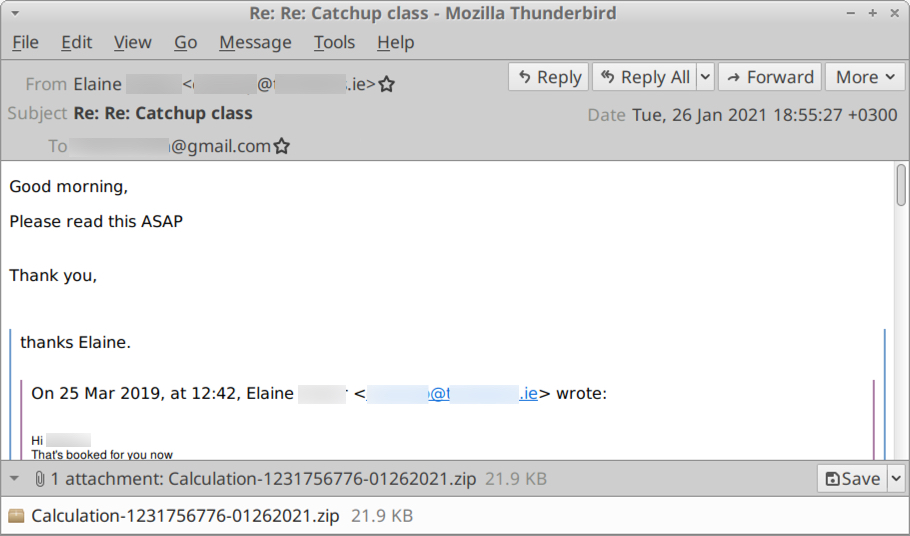
Shown above: One of the emails exported from the pcap (a copy is available here).
Notes
This month, the affiliate or campaign identification string for Qakbot malware distributed through TA551 has been krk01. When my krk01 Qakbot-infected host started spamming more Qakbot, the affiliate/campaign ID for Qakbot samples caused by this malspam was abc120.
Because of this and its previous history pushing different families of malware, I believe TA551 (Shathak) is a distributor for other criminals in our cyber threat landscape. The other criminals push malware (like the criminals behind Qakbot), while TA551 is specifically a distribution network.
Indicators of Compromise (IOCs)
SHA256 hash: 17cd3c11fba639c1fe987a79a1b998afe741636ac607254cc134eea02c63f658
- File size: 76,663 bytes
- File name: particulars-01.26.21.doc
- File description: TA551 (Shathak) Word doc with macros for Qakbot (Qbot)
SHA256 hash: 231b081480a80b05d69ed1d2e18ada8a1fd85ba6ce3e69cc8f630ede5ce5400e
- File size: 888,832 bytes
- File location: hxxp://5that6[.]com//assets/55ddb775/ce51025b12/9b75bbce/8a06fd47/6ac84e7424b0539286562b/xtuaq14?anz=125c5909&dlzwg=7aec167a5a2ab0&bu=a09f740
- File location: C:ProgramDataaZe4I.tmp
- File description: Windows malware DLL retrieved by Word macro, used to install Qakbot (Qbot) affliate/campaign ID krk01
- Run method: regsvr32.exe [filename]
Final words
A pcap of the infection traffic and and malware from the infected Windows host can be found here.
—
Brad Duncan
brad [at] malware-traffic-analysis.net
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License. Read More
The post TA551 (Shathak) Word docs push Qakbot (Qbot), (Tue, Jan 26th) appeared first on Malware Devil.
https://malwaredevil.com/2021/01/26/ta551-shathak-word-docs-push-qakbot-qbot-tue-jan-26th/?utm_source=rss&utm_medium=rss&utm_campaign=ta551-shathak-word-docs-push-qakbot-qbot-tue-jan-26th






















