Let’s first take a look back at 2020!
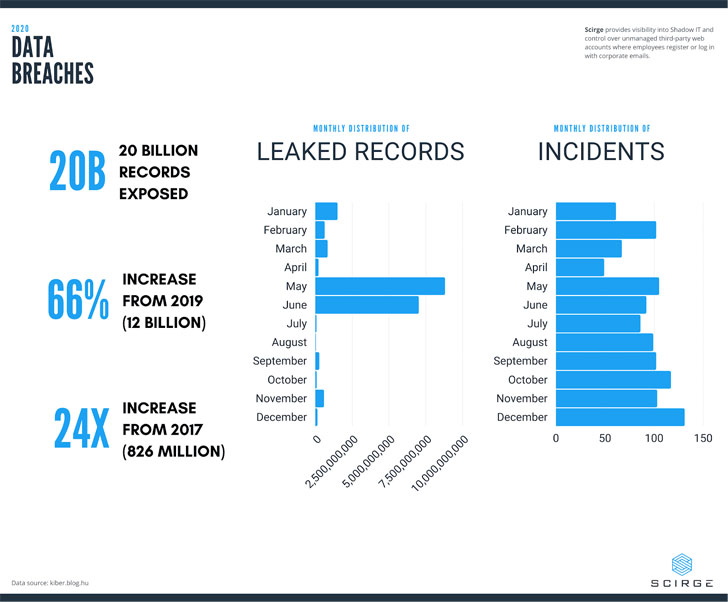
Adding to the list of difficulties that surfaced last year, 2020 was also grim for personal data protection, as it has marked a new record number of leaked credentials and PI data.
A whopping 20 billion records were stolen in a single year, increasing 66% from 12 billion in 2019. Incredibly, this is a 9x increase from the comparatively “small” amount of 2.3 billion records stolen in 2018.
This trend seems to fit an exponential curve; even worse, we are yet to see the fallouts from the end of the year “Solorigate” campaign, which has the potential to marginalize even these numbers by the end of 2021.
Found among the leaked data are usernames, passwords, credit card numbers, bank account details, healthcare information, and other personal data. Malicious actors utilize these treasure troves of information for fraud and further attacks.
In just the first quarter of 2020, the Dutch government managed to lose a hard drive containing confidential citizen data. Meanwhile, the UK government exposed 28 million children’s data to betting companies, and Microsoft exposed 250 million records of customer support–including customers’ geographic data, IP addresses, and other private information.
By April, Zoom had lost 500,000 passwords at the start of the global remote working period. In June of Q2, Oracle had also leaked billions of web tracking data by storing data on an unsecured server.
Q3 kicked off with Joe Biden’s campaign app exposing millions of users’ sensitive voter data. This was followed by 300,000 Spotify users falling victim to account takeover attempts after their credentials were made public.
The year ended with Solorigate: an incident with a lasting impact that has yet to be fully seen. Ultimately, 2020 closed with a total of 1,114 incidents, with several governments and well-known brands–such as Estee Lauder, Marriott, Nintendo, and GoDaddy–involved in large-scale breaches.
Why are companies and organizations still failing?
This trend of data breaches is quite disappointing when compared to the staggering $120 Billion in global IT security spending; according to Gartner, this number has grown each year rapidly.
The only possible solution to this inconsistency rests in user awareness and the possibility that existing technologies are missing something substantial to turn the tide on these trends.
The most common cause behind data breaches is the leak of some authentication measure–this may be a username, password, token, API-key, or a negligent password-less server or application.
Users are registering to third-party websites and services with corporate email addresses and credentials every day. In tandem, they create massive blind spots in visibility and a field of Shadow IT that no audit or security tool has been able to mitigate thus far. Each employee has around 200 accounts–for every 1,000 employees, that is 200,000 potentially unknown or weak passwords, many of which may be corporate related.
Once these third parties get compromised, the credentials obtained might be reused to gain unauthorized access to other corporate services, such as email accounts or VPN servers, using attack techniques like credential stuffing or password spraying.
This was exactly the case with British Airways, which received a record GDPR fine of GBP20 million after 400,000 passengers’ data was breached, initiated through a VPN gateway accessed by a compromised account.
Most large organizations use data leak prevention technologies yet fail to protect against password leaks and account takeovers. This demonstrates an apparent need for a new approach–a hybrid of technological controls and immediate user awareness improvement that implements a fresh perspective on account protection.
Shedding Light on Shadow IT
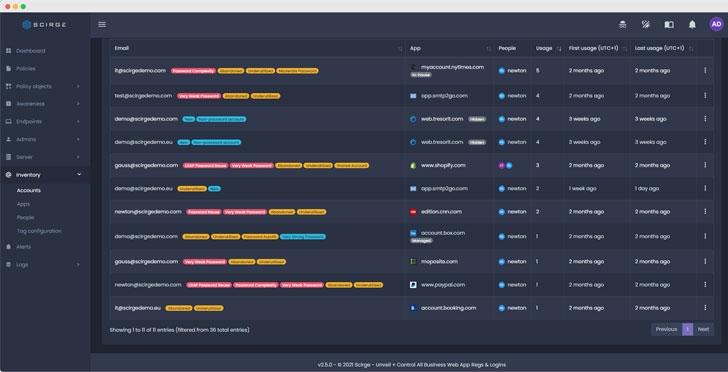
Scirge was developed with a simple and clear focus on solving an overlooked aspect of existing IT security mechanisms: discovering and protecting accounts created by employees in the cloud. This includes the capability to monitor all new registrations, as well as viewing logins with existing credentials to websites and web applications.
Furthermore, it involves centrally managed strength and complexity checks for all passwords while also warning users for proper credential management.
Policy-based controls may be created to block the usage of certain email addresses or websites. Scirge will immediately provide users with awareness messages when they are misusing corporate credentials or disregarding password complexity requirements.
Central intelligence helps unveil reused passwords and compromised accounts via comparing every company-related account to leak databases and locally-used (Active Directory) accounts. Scirge can illuminate organizations’ otherwise hidden cloud footprint while simultaneously empowering users with knowledge about password hygiene, corporate policies, and unwanted behavior when using corporate accounts.
Scirge accomplishes each of these goals with a clean, browser-based approach. It eliminates the need to control or view network traffic, decrypt SSL, or burden clients with full-blown agents–a common source of performance degradation and compatibility issues with other security tools.
Utilizing its unique features, Scirge creates visibility for all employee-created accounts and reveals password hygiene issues. Inventory for all users–including departing workers–is readily available, unveiling unwanted account sharing between users and potential insider threats of misusing identities when accessing online resources.
The dashboard also shows IT management what cloud apps are most used without consent, helping the company comply with regulations via collecting privacy policies and T&Cs of all services.
Learn more about account protection and Shadow IT awareness here or register to one of our webinars.
Found this article interesting? Follow THN on Facebook, Twitter and LinkedIn to read more exclusive content we post.
Read More
The post Why do companies fail to stop breaches despite soaring IT security investment? appeared first on Malware Devil.
https://malwaredevil.com/2021/03/01/why-do-companies-fail-to-stop-breaches-despite-soaring-it-security-investment/?utm_source=rss&utm_medium=rss&utm_campaign=why-do-companies-fail-to-stop-breaches-despite-soaring-it-security-investment