
PrismHR, a company that sells technology used by other firms to help more than 80,000 small businesses manage payroll, benefits, and human resources, has suffered what appears to be an ongoing ransomware attack that is disrupting many of its services.
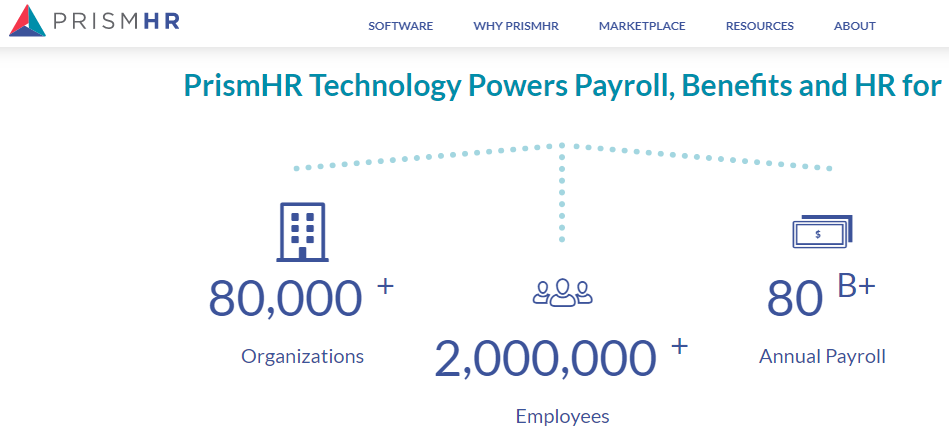
Hopkinton, Mass.-based PrismHR handles everything from payroll processing and human resources to health insurance and tax forms for hundreds of “professional employer organizations” (PEOs) that serve more than two million employees. The company processes more than $80 billion payroll payments annually on behalf of PEOs and their clients.
Countless small businesses turn to PEOs in part because they simplify compliance with various state payroll taxes, and because PEOs are the easiest way for small businesses to pool their resources and obtain more favorable health insurance rates for their employees.
PrismHR has not yet responded to requests for comment. But in a notice sent to its PEO partners, PrismHR said it detected suspicious activity within its networks on Feb. 28, and that it disabled access to its platform for all users in an effort to contain the security incident.
The company said the disruption has affected 200 PEO clients across the country, and that the most immediate concern is helping PEOs ensure their customers can process payrolls this week.
“The outage may extend throughout today and possibly later, with potential impact on payroll processing,” Prism explained in a template email it suggested PEO partners share with their customers. “We are committed to ensuring everyone receives their pay as timely and as accurately as possible. For this payroll period, we will use estimates from the last available payroll period. Once the software platform is back online, we will perform a reconciliation and correct any discrepancies as soon as possible.”
Jacob Cloran is co-founder of Decimal, a company that does accounting for small businesses, many of whom rely on PEOs affected by the PrismHR outage. Decimal itself uses a PEO that relies on PrismHR.
“We don’t have a good option to run our payroll this week, and the message we’ve received from our PEO doesn’t give me a lot of confidence we’ll be able to do that,” Cloran said.
Cloran said while there are other cloud-based companies that work with multiple PEOs, PrismHR is by far the largest.
“Prism is the only real option on the PEO software market,” he said. “Everyone I know who has tried any of the others ends up back at Prism. It’s the best of all bad available options.”
PrismHR did not specify what was responsible for the suspicious network activity, but their actions so far are straight out of the textbook recommendations for responding to a ransomware outbreak. A notice from the PEO working with some of Cloran’s clients stated that PrismHR was in the process of rebuilding its entire system from data backups in a new environment.
Also, the crooks behind ransomware attacks typically wait until the weekend to unleash their malware within victim organizations, knowing that most targets will be short-staffed or out of the office at this time. PrismHR said it detected the activity on Sunday.
Ransomware victims perhaps in the toughest spot include those providing cloud data hosting and software-as-service offerings, as these businesses are often unable to serve their customers while a ransomware infestation is active.
Ransomware renders any files it touches unreadable unless and until a victim pays for a digital key needed to unlock the encryption on them. Worse, it has become almost a best practice among ransomware criminal groups to steal as much data as possible from the victim organization prior to unleashing the ransom malware within a target environment.
Some of that data is often then published on dark web victim shaming sites in a bid to force the victim company into paying up. Some companies victimized by ransomware even face dual ransom demands: One for a digital key needed to unlock access to files, and a second payment in exchange for a promise not to publish all of the stolen data. Those that refuse to be extorted are told to expect that huge amounts of sensitive company data will be published online or sold on the dark web (or both).
PrismHR said in a statement to its PEO customers that while its investigation and response to the incident is ongoing, the company “is not aware of any sensitive data being breached or compromised.”
Given the volume and sensitive nature of the data PrismHR managed on behalf of PEO clients, it’s no doubt those clients and their customers are hoping that statement is accurate as well.
Read More
The post Payroll/HR Giant PrismHR Hit by Ransomware? appeared first on Malware Devil.
https://malwaredevil.com/2021/03/02/payroll-hr-giant-prismhr-hit-by-ransomware/?utm_source=rss&utm_medium=rss&utm_campaign=payroll-hr-giant-prismhr-hit-by-ransomware



























