
I like taking a closer look at captures files posted by Brad. In his latest diary entry, we have a capture file with Cobalt Strike traffic.
With regular expression “^/….$” I look for URIs that are typical for Cobalt Strike shellcode (and Metasploit too):
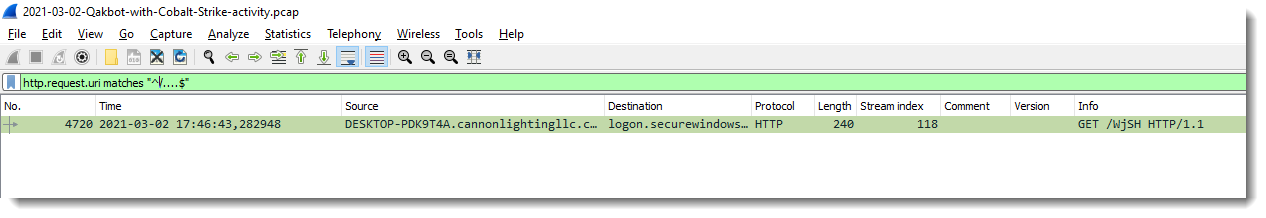
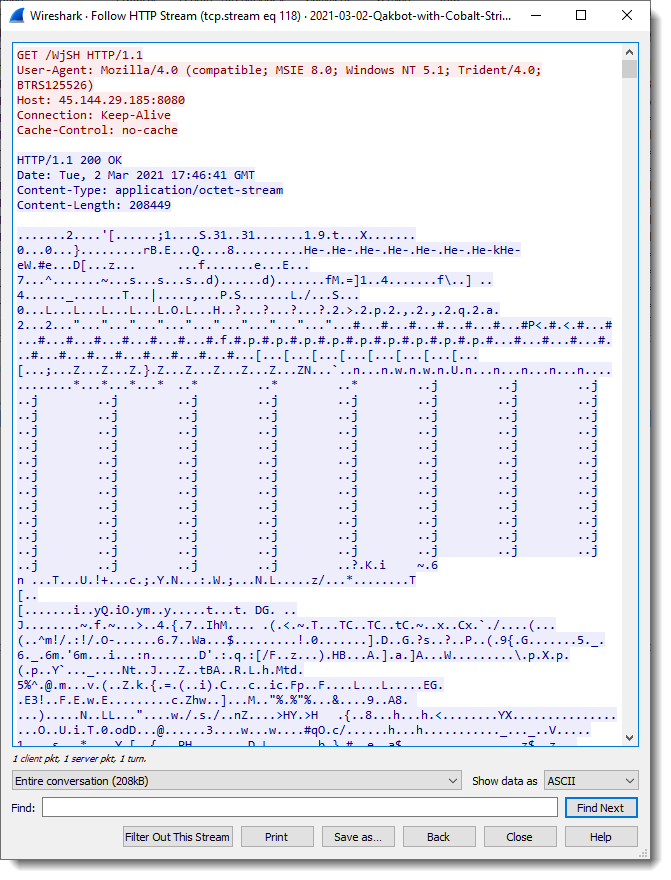
Following this HTTP stream, I see data that looks encoded and has some repetitions, so this might be some kind of XOR encoding:
I export this data stream as a file:
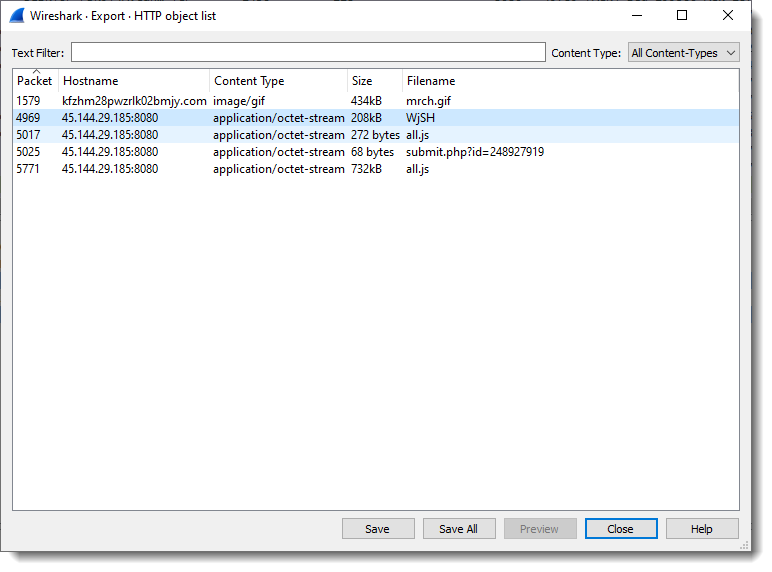
Then pass it through my 1768.py Cobalt Strike beacon analysis tool:
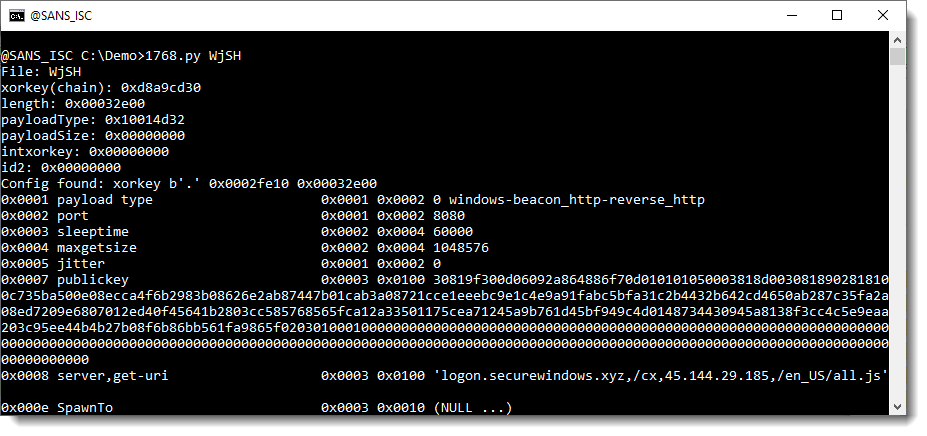
And this is indeed the configuration of a beacon.
Didier Stevens
Senior handler
Microsoft MVP
blog.DidierStevens.com DidierStevensLabs.com
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License. Read More
The post PCAPs and Beacons, (Sun, Mar 7th) appeared first on Malware Devil.
https://malwaredevil.com/2021/03/07/pcaps-and-beacons-sun-mar-7th/?utm_source=rss&utm_medium=rss&utm_campaign=pcaps-and-beacons-sun-mar-7th

No comments:
Post a Comment